
Compliance in healthcare is paramount, representing adherence to laws and regulations, such as HIPAA. This adherence is crucial for safeguarding patient information and maintaining operational integrity. Understanding compliance is essential for CFOs, as it directly impacts financial performance, risk management, and the organization's reputation. The severe consequences of non-compliance cannot be overstated; they include financial penalties and a significant loss of stakeholder trust. In a landscape increasingly fraught with regulatory challenges, CFOs must prioritize compliance to ensure their organizations thrive.
In the intricate world of healthcare, compliance stands as a fundamental pillar safeguarding both patient information and organizational integrity. For CFOs navigating the complexities of financial strategy, grasping compliance is not merely about adhering to regulations; it represents a vital opportunity to enhance operational resilience and financial performance. Yet, as regulatory landscapes evolve, the pressing question arises: how can healthcare leaders ensure their organizations not only meet these standards but also leverage compliance as a strategic advantage in an increasingly competitive environment?
In discussing the operation of any company, particularly within the medical field, it is essential to understand that what is integral, as is paramount. The sensitive nature of patient information necessitates strict regulations, such as the , designed to protect it.
For CFOs, grasping the is essential, as it directly influences budget planning, risk management, and the overall operational integrity of healthcare institutions. Understanding the means what can be severe, leading to significant penalties, legal ramifications, and reputational damage. This makes it important for financial strategists to understand what compliance means.
The fallout from failing to meet regulatory standards can be particularly damaging; for instance, healthcare organizations may suffer following a data breach. Moreover, maintaining compliance is not merely a regulatory requirement; it serves as a strategic advantage. Organizations that prioritize adherence can create an equitable environment for data protection, ensuring consistent security measures that mitigate risks associated with .
As industry experts emphasize, are vital to keep pace with increasingly sophisticated cybercriminals. Therefore, understanding and implementing regulatory measures transcends the goal of avoiding penalties; it is fundamentally about , which raises the question of what compliance means.
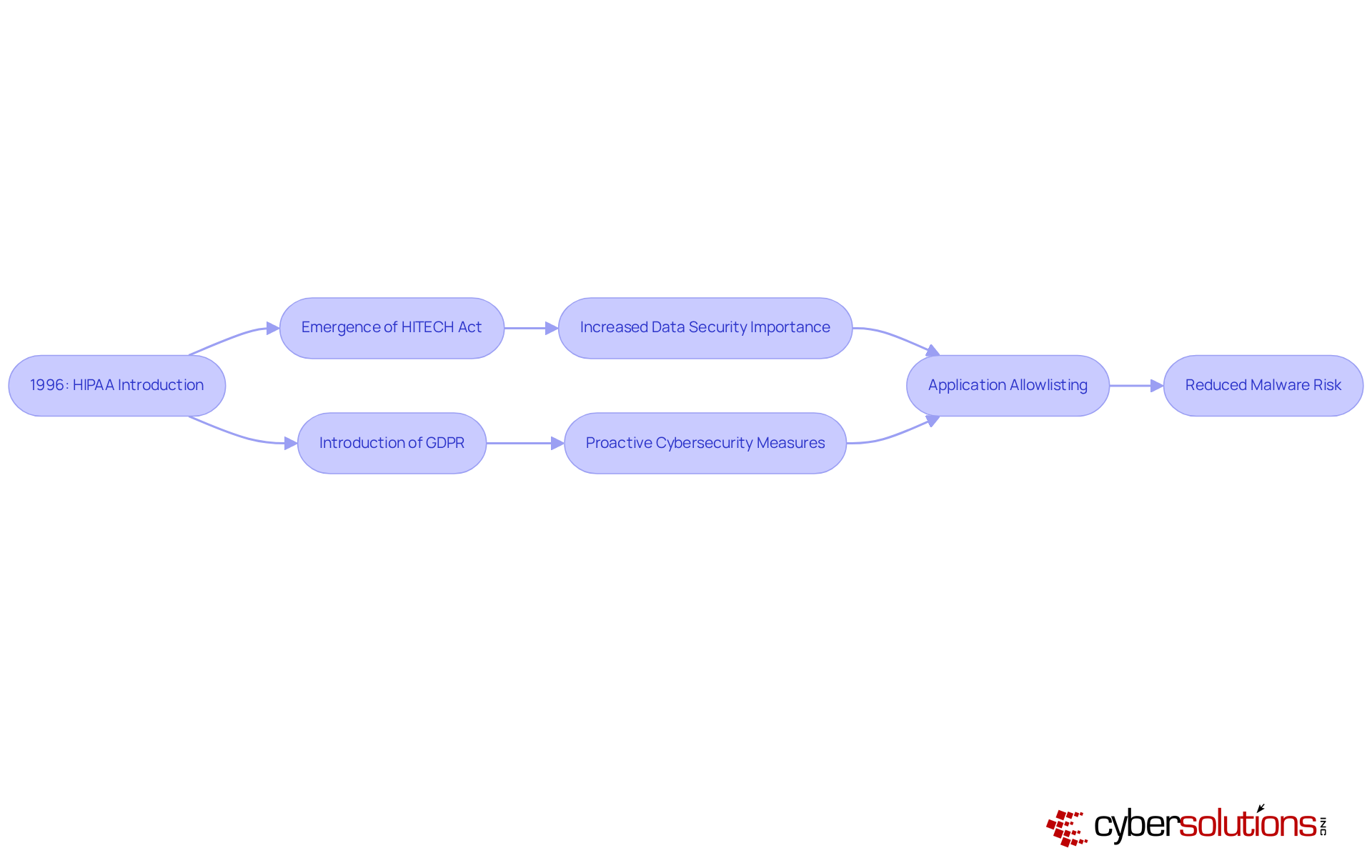
In today's rapidly evolving landscape, the significance of cybersecurity in healthcare cannot be overstated. The transformation of the concept of has occurred dramatically over the decades, particularly in response to various scandals and crises that have revealed vulnerabilities in organizational practices. A pivotal moment occurred with the introduction of in 1996, which established national standards for the protection of health information. As we have progressed, additional regulations such as the HITECH Act and GDPR have emerged, underscoring the increasing importance of .
This historical context highlights the to remain vigilant and informed about . The implementation of proactive , particularly , is essential for ensuring that compliance means what it entails in relation to these regulations. Application allowlisting not only prevents unauthorized software from running but also helps organizations understand compliance means what by enforcing rigorous control over software usage to meet stringent regulatory demands.
Moreover, this proactive approach significantly diminishes the risk of malware, enhancing overall data security. For medical facilities aiming to protect sensitive information, application allowlisting emerges as a crucial strategy. Are your cybersecurity measures robust enough to withstand the evolving threats? The time to act is now—prioritize compliance and security to safeguard your organization and its patients.
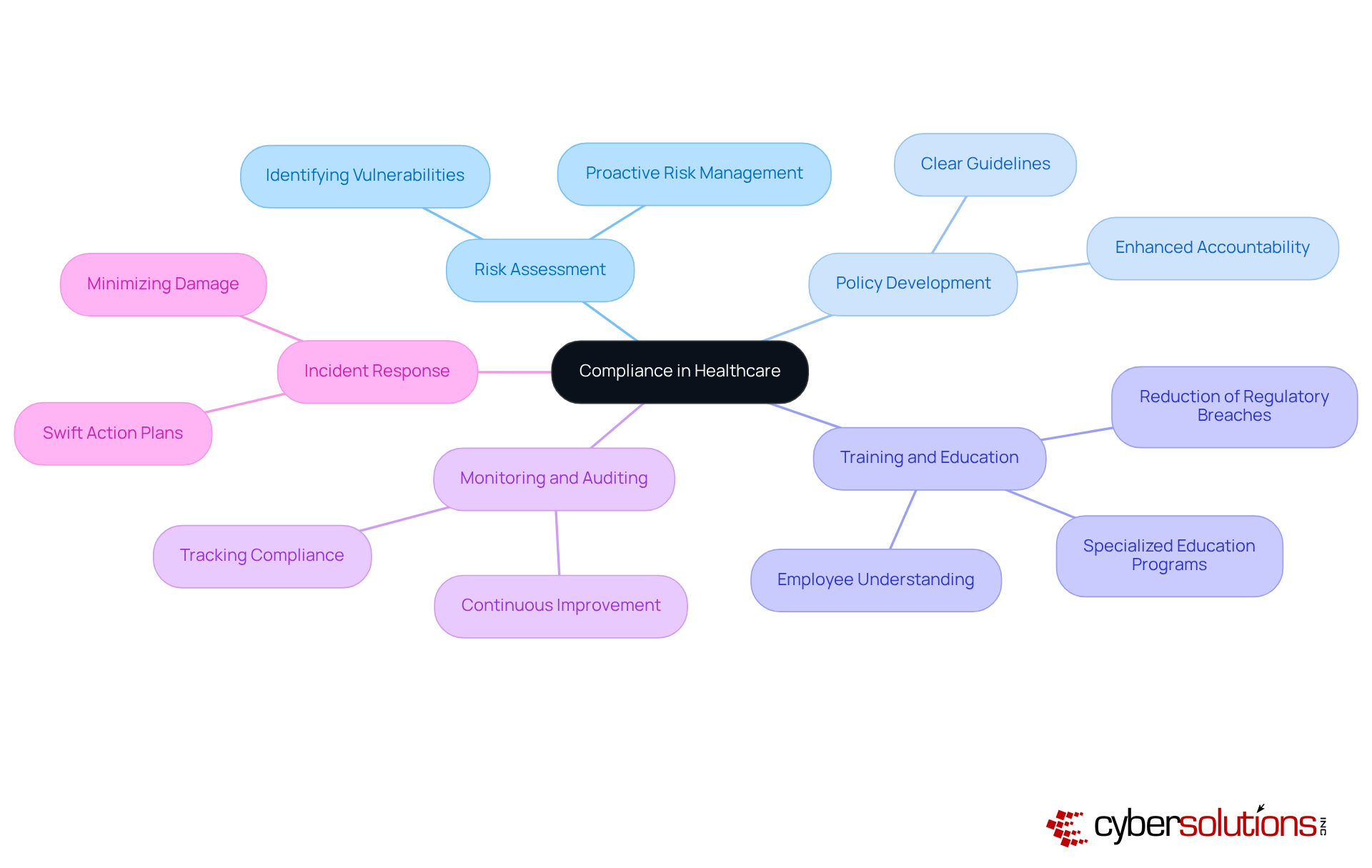
In the realm of healthcare, adherence is paramount, encompassing , policy development, , , and . Risk assessment stands as a cornerstone, essential for identifying potential vulnerabilities and threats to patient data. This proactive approach enables organizations to address risks before they escalate, safeguarding both patients and the integrity of healthcare systems. Policy development establishes clear guidelines for , providing a structured framework for staff to follow, thereby enhancing accountability and clarifying what .
Training and education are critical components, equipping employees with a comprehensive understanding of their responsibilities. Research indicates that effective training significantly reduces . For instance, have been shown to enhance medical workers' knowledge and adherence to safety protocols, particularly in high-stakes areas like chemotherapy medication preparation.
Furthermore, monitoring and auditing play a vital role in tracking adherence to regulations. These processes allow organizations to identify and ensure continuous alignment with established standards. An effective incident response plan is equally crucial, enabling swift action in the face of breaches or violations, thereby minimizing potential damage. Together, these elements form a that not only protects patient well-being but also fosters a culture of responsibility and excellence in service delivery.
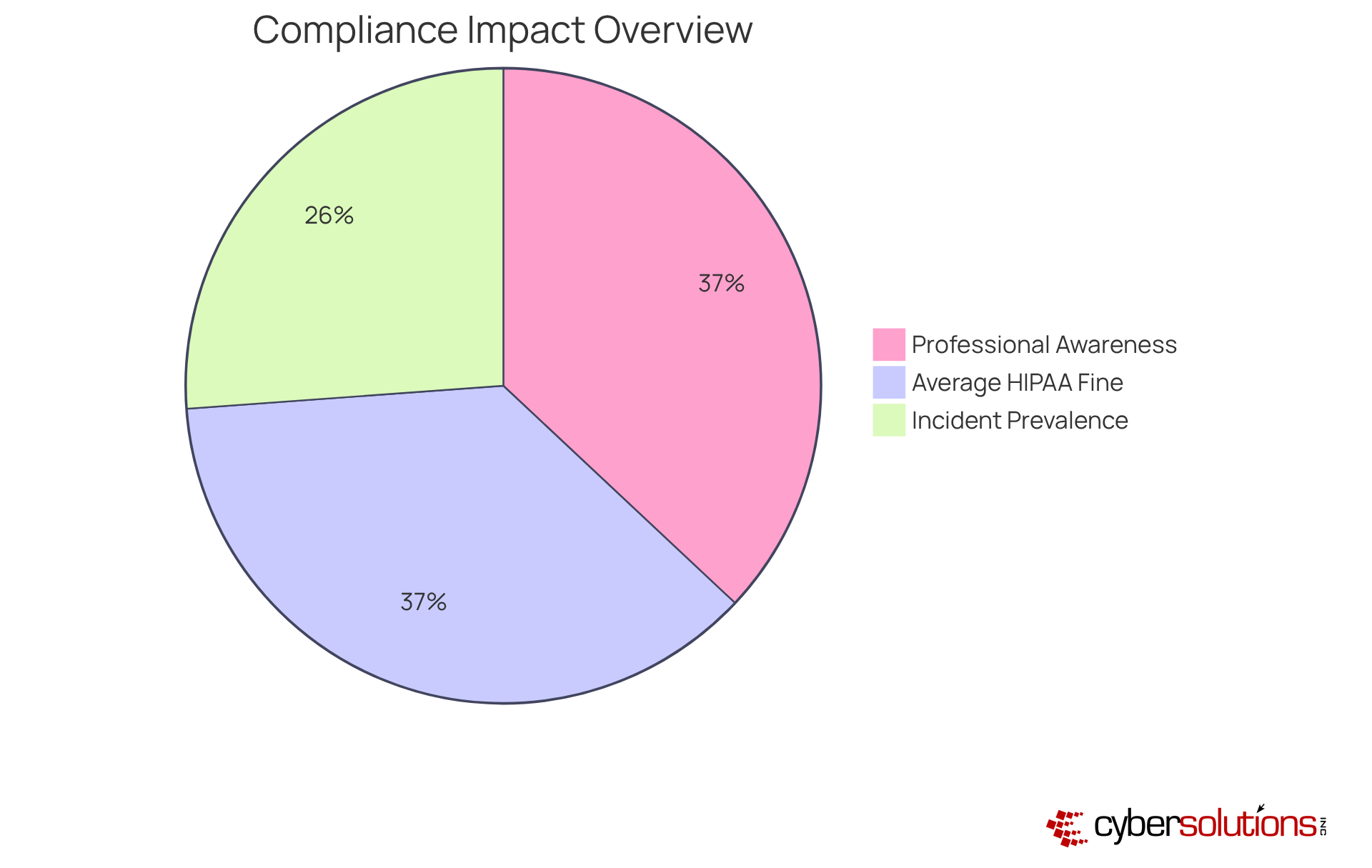
Understanding compliance means what goes beyond mere regulatory obligation; it stands as a cornerstone of for healthcare organizations. For CFOs, efficient adherence management significantly enhances monetary performance by mitigating the risk of substantial penalties and legal costs associated with non-adherence. In fact, the average HIPAA fine in 2022 was $98,643, underscoring the .
Furthermore, a robust regulatory framework fosters trust among patients and stakeholders, which is essential for bolstering an organization’s reputation and competitive advantage. Research indicates that 99% of healthcare professionals recognize the importance of to their business operations, yet many encounter challenges with effective implementation.
Organizations that prioritize are not only better equipped to but also experience enhanced and . This is particularly critical in a sector where 70% of entities reported experiencing an incident in the past year, highlighting the necessity for .
By cultivating a means what, healthcare organizations can elevate patient trust, leading to improved treatment adherence and ultimately better patient outcomes.
Understanding compliance in the healthcare sector is not merely about adhering to regulations; it is a fundamental aspect that shapes the operational integrity and financial stability of organizations. For CFOs, grasping the nuances of compliance is crucial, as it directly impacts budget planning, risk management, and the overall health of healthcare institutions. The consequences of non-compliance can be severe, ranging from hefty fines to reputational damage, underscoring the need for a comprehensive understanding of what compliance truly entails.
The evolution of compliance has been significant, tracing its historical roots with the introduction of regulations like HIPAA to the contemporary challenges posed by cyber threats. Key components such as risk assessment, policy development, and ongoing training are essential for fostering a culture of compliance. Moreover, proactive measures like application allowlisting are vital in safeguarding sensitive patient information. By integrating these elements, healthcare organizations can not only meet regulatory requirements but also enhance their operational efficiency and build trust with patients and stakeholders.
Ultimately, the significance of compliance in healthcare extends beyond merely avoiding penalties; it is about creating a secure environment that prioritizes patient data protection and promotes organizational resilience. Healthcare CFOs are called to champion compliance as a strategic advantage, ensuring their organizations not only survive but thrive in an increasingly complex regulatory landscape. By embracing a proactive compliance strategy, healthcare organizations can pave the way for improved patient outcomes and a more trustworthy healthcare system.
What does compliance mean in the context of healthcare?
Compliance in healthcare refers to adherence to laws, regulations, guidelines, and specifications that are crucial for the operation of medical companies, particularly regarding the protection of sensitive patient information.
Why is compliance important for CFOs in healthcare organizations?
For CFOs, understanding compliance is essential as it impacts budget planning, risk management, and the overall operational integrity of healthcare institutions. Non-compliance can lead to severe penalties, legal issues, and damage to the organization's reputation.
What are the consequences of failing to meet regulatory standards in healthcare?
Failing to meet regulatory standards can result in substantial financial losses, a decline in stakeholder trust, and potential legal ramifications for healthcare organizations, especially following incidents like data breaches.
How does maintaining compliance serve as a strategic advantage for organizations?
Maintaining compliance not only fulfills regulatory requirements but also creates a secure environment for data protection. Organizations that prioritize compliance can implement consistent security measures that help mitigate risks associated with cyber threats.
What role does ongoing education play in compliance?
Ongoing education and remediation are vital for keeping up with increasingly sophisticated cybercriminals. Understanding and implementing regulatory measures is crucial for safeguarding an organization’s financial health and operational resilience, beyond merely avoiding penalties.