
In today's digital landscape, the importance of robust cybersecurity measures in healthcare cannot be overstated. Healthcare CFOs must prioritize effective data backup practices to safeguard sensitive information and ensure business continuity amidst the growing threat of cyberattacks. The financial implications of data breaches are staggering, with an estimated cost of $7.42 million per incident. To mitigate these risks, CFOs should:
These measures will help protect patient health information and reinforce their organizations' resilience against potential threats.
In the healthcare sector, the stakes of data management and security have reached unprecedented heights. With potential costs of data breaches soaring into millions, CFOs are tasked with the imperative of implementing robust corporate data backup practices to protect sensitive information. This article explores the essential strategies healthcare leaders must adopt to not only shield their organizations from cyber threats but also ensure compliance with regulatory standards. Yet, as organizations invest in these protective measures, a critical question arises:
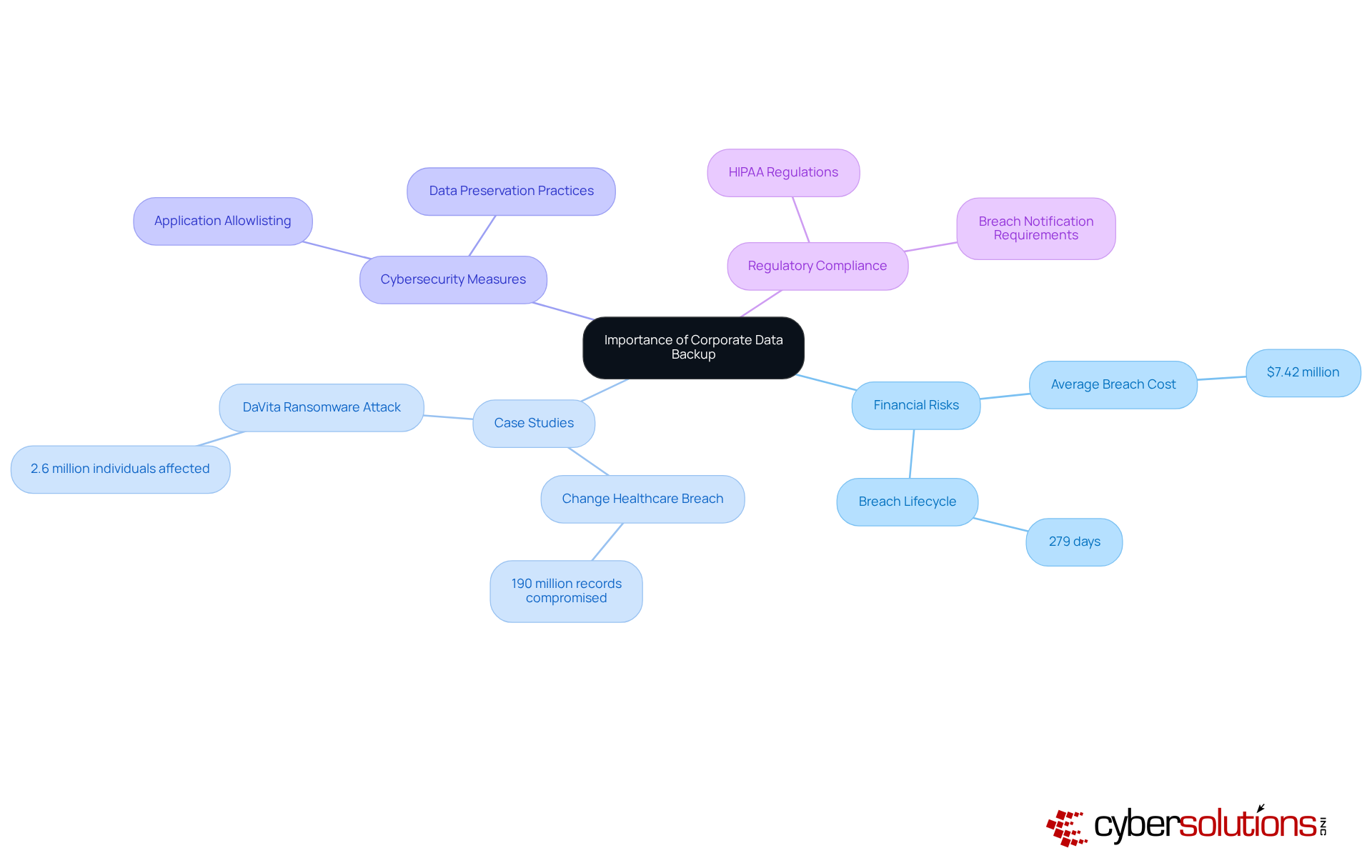
In the medical field, efficient information management is not just important; it is essential. Corporate data backup serves as the foundation of risk management, particularly in an era where data breaches pose severe financial threats. Consider this: the typical expense of a medical information breach in 2025 is estimated at $7.42 million. This staggering figure reflects a considerable financial strain on organizations, emphasizing the urgency for robust cybersecurity measures. Furthermore, the average breach lifecycle in healthcare spans 279 days, leading to increased recovery costs and operational disruptions. The erosion of trust among patients and stakeholders due to lost patient information cannot be underestimated.
A case study on the Change Healthcare breach illustrates the disastrous effects of inadequate protection measures. This incident compromised information for approximately 190 million individuals, resulting in substantial financial fallout for the organization. Thus, it is imperative for CFOs to prioritize , including corporate data backup, to safeguard sensitive information and ensure business continuity. Investing in reliable corporate data backup solutions and implementing application allowlisting are effective strategies to mitigate risks associated with malware and unauthorized software, thereby protecting financial health amidst escalating cyber threats.
Application allowlisting features, such as continuous monitoring and centralized management, significantly enhance security by ensuring that only approved applications can operate. This not only aids adherence to HIPAA regulations but also fortifies the organization against potential breaches. As Joe Oleksak emphasizes, cybersecurity must be integrated into the organizational DNA, highlighting the essential role of information management in financial strategy.
Moreover, comprehensive HIPAA adherence solutions, including proactive risk management and audit assistance, are vital for healthcare organizations to uphold regulations and protect patient health information. The time to act is now; the stakes are high, and the consequences of inaction are too severe to ignore.
In today's healthcare landscape, the importance of cybersecurity cannot be overstated. Healthcare CFOs must conduct a comprehensive evaluation to identify critical information that requires protection, with a particular focus on:
By classifying information based on its significance and sensitivity, organizations can develop a prioritized corporate data backup plan that not only secures vital details but also adheres to robust cybersecurity practices. For instance, patient records should be backed up more frequently than less critical information, ensuring that the most crucial data remains protected.
To bolster information security, organizations should implement:
Understanding the regulatory landscape, including the implications of , can aid CFOs in pinpointing which categories of information related to corporate data backup are subject to specific regulations, thereby guiding their backup prioritization. Furthermore, integrating proactive risk management and audit assistance into the recovery plan will enhance information security and ensure readiness for any compliance audits.
In this ever-evolving threat environment, are you prepared to safeguard your organization’s most sensitive information? By taking decisive action now, healthcare CFOs can not only protect their organizations but also foster a culture of security that resonates throughout their teams.

In today's healthcare landscape, the importance of robust data recovery strategies cannot be overstated. CFOs in the medical field must embrace a multi-layered approach that integrates both on-site and cloud-based storage solutions, ensuring redundancy and resilience. On-site copies facilitate rapid access to vital information, crucial for operational continuity, while cloud storage provides essential off-site protection against physical disasters and data loss. By utilizing hybrid recovery strategies, organizations can significantly enhance their information restoration capabilities, particularly in meeting stringent medical regulations, including HIPAA.
Establishing a consistent save routine is imperative; data should be saved frequently enough to mitigate potential losses. Automated recovery solutions streamline this process, substantially reducing the risk of human error, which accounts for 43% of breaches in the medical sector. Moreover, encrypting stored data is vital to safeguard against unauthorized access, further ensuring compliance with regulations such as HIPAA. Experts assert that a robust data recovery plan not only protects sensitive patient information but also bolsters overall operational effectiveness, making it an essential investment for medical institutions in 2025.
Routine are crucial to ensure these solutions function correctly and that data copies are executed as intended. In addressing potential challenges, healthcare CFOs must remain vigilant regarding the complexities of managing both on-site and cloud solutions to prevent misapplication of the multi-layered recovery strategy. Proactive risk management, coupled with expert guidance—such as virtual CISO services—can further enhance ongoing compliance and cybersecurity management.

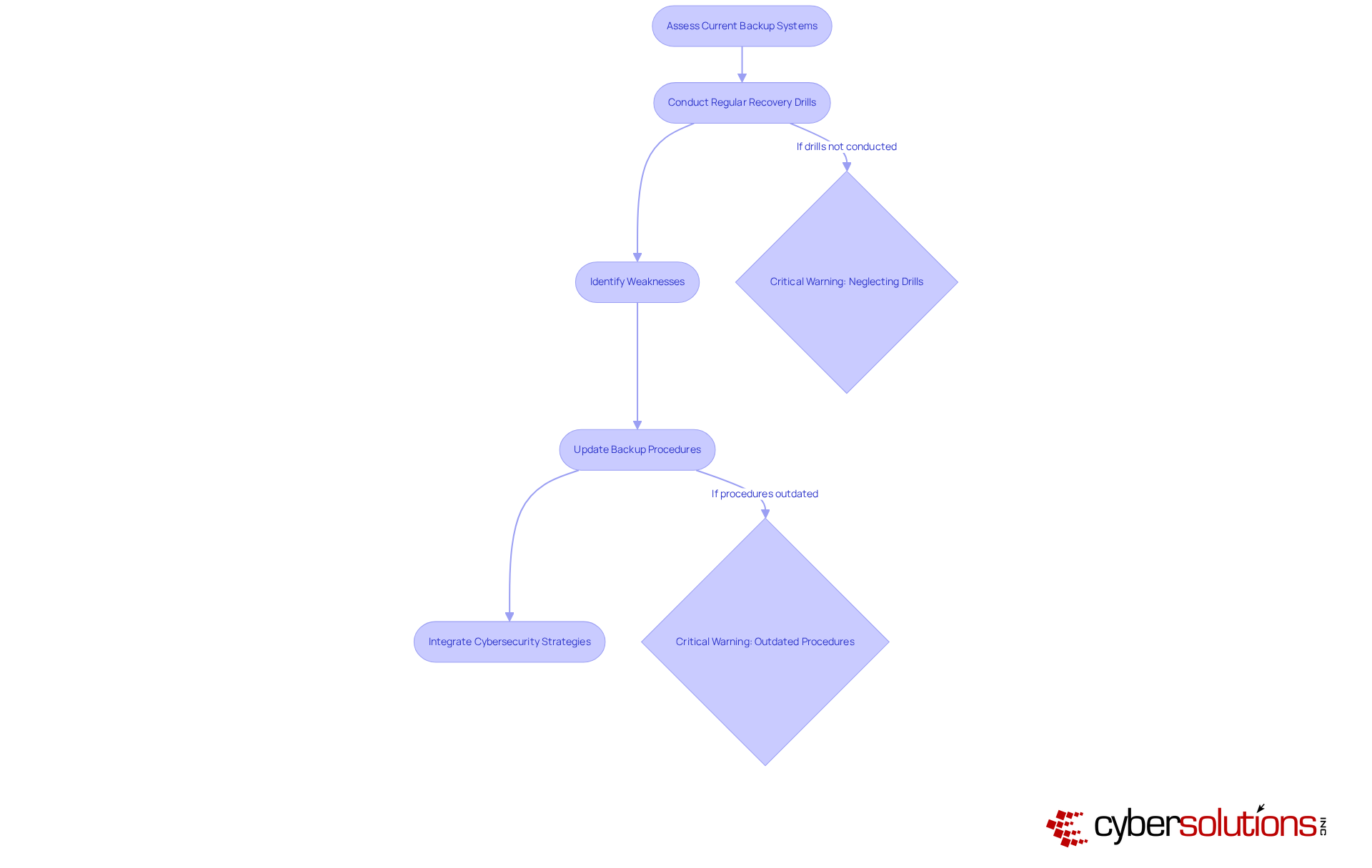
In today's healthcare landscape, establishing robust support systems for cybersecurity is not just important—it's imperative. Organizations must regularly test and update these systems to ensure their effectiveness. Regular recovery drills are vital; these simulations empower teams to identify weaknesses in backup procedures and refine their response strategies. Alarmingly, a significant percentage of medical organizations still neglect to conduct these critical drills, leaving them vulnerable during actual data loss events.
A recent case study underscores this point: Cyber Solutions Inc. successfully restored 4,500 endpoints following a ransomware attack, demonstrating how rapid incident response and specialized expertise can enhance recovery efforts and ensure continuity of care. This incident highlights the necessity of a and the importance of taking immediate action to contain threats.
As technology evolves, refreshing storage systems to incorporate the latest security features and comply with regulatory standards, particularly those mandated by HIPAA, becomes essential. By adopting a proactive approach to corporate data backup management and integrating comprehensive cybersecurity strategies—including 24/7 network monitoring and alert services to detect anomalies—CFOs can significantly bolster their organization's resilience against data loss, ensure compliance with regulatory standards, and ultimately safeguard patient information while maintaining operational continuity.
Robust corporate data backup practices are not merely a technical requirement for healthcare CFOs; they are a critical component of an organization's financial strategy and risk management framework. The healthcare sector faces unique challenges, including severe financial repercussions from data breaches and the erosion of patient trust. Therefore, prioritizing effective data backup solutions is essential to safeguard sensitive information and ensure operational continuity.
In today's landscape, the threats to cybersecurity are ever-evolving, making it imperative for healthcare organizations to adapt. The implications of inadequate data protection can be devastating, leading to not only financial losses but also a significant decline in patient trust. By implementing strong data backup practices, healthcare organizations can mitigate these risks and reinforce their commitment to security.
Throughout this article, key strategies have been outlined, including:
By classifying data according to its significance, adopting a multi-layered recovery approach, and conducting routine recovery drills, healthcare organizations can significantly enhance their resilience against data loss and compliance risks. The insights provided underscore the importance of integrating cybersecurity into the organizational framework, which is vital for maintaining trust and financial stability.
Ultimately, the call to action is clear: healthcare CFOs must recognize the urgency of implementing strong data backup practices. By taking decisive steps to protect their organizations' most sensitive information, they not only comply with regulatory requirements but also foster a culture of security that resonates throughout their teams. Embracing these best practices will not only mitigate risks but also position healthcare organizations for success in an increasingly complex digital landscape.
Why is corporate data backup important in the medical field?
Corporate data backup is essential in the medical field as it serves as a foundation for risk management, protecting organizations from the severe financial threats posed by data breaches.
What is the estimated cost of a medical information breach in 2025?
The typical expense of a medical information breach in 2025 is estimated to be $7.42 million.
How long does the average breach lifecycle last in healthcare?
The average breach lifecycle in healthcare spans 279 days.
What are the consequences of lost patient information for healthcare organizations?
Lost patient information can lead to erosion of trust among patients and stakeholders, increased recovery costs, and operational disruptions.
Can you provide an example of the impact of inadequate data protection measures?
The Change Healthcare breach compromised information for approximately 190 million individuals, resulting in substantial financial fallout for the organization.
What strategies should CFOs prioritize to safeguard sensitive information?
CFOs should prioritize strong data preservation practices, including corporate data backup and investing in reliable backup solutions.
How does application allowlisting enhance cybersecurity?
Application allowlisting enhances cybersecurity by ensuring that only approved applications can operate, which aids in adherence to HIPAA regulations and protects against potential breaches.
What are some features of application allowlisting?
Features of application allowlisting include continuous monitoring and centralized management.
Why is it important for healthcare organizations to adhere to HIPAA regulations?
Adherence to HIPAA regulations is vital for protecting patient health information and ensuring compliance with legal standards.
What proactive measures can healthcare organizations take to manage risks?
Healthcare organizations should implement comprehensive HIPAA adherence solutions, including proactive risk management and audit assistance.