
In today's rapidly evolving medical landscape, implementing effective IT solutions is paramount for healthcare organizations. This article outlines four best practices that are essential for success:
By focusing on stakeholder engagement and clear goal definitions, these practices ensure that IT systems effectively support patient care and operational efficiency. Tailored training programs and regular audits play a critical role in this process, enabling healthcare providers to navigate the unique challenges they face. Embracing these strategies not only enhances operational effectiveness but also fosters a culture of continuous improvement, ultimately leading to better patient outcomes.
The healthcare landscape is rapidly evolving, propelled by technological advancements and an escalating demand for efficient patient care. As organizations endeavor to enhance their IT solutions, grasping best practices becomes essential for aligning technology with business objectives. Yet, with a plethora of options at their disposal, how can healthcare providers guarantee that they are making informed decisions that not only address current needs but also anticipate future challenges? This article explores critical strategies for optimizing IT solutions in healthcare, providing insights that can significantly enhance operational effectiveness and ultimately elevate patient outcomes.
To effectively assess organizational needs for IT solutions, healthcare providers must engage in a comprehensive evaluation process that includes several critical steps:
By adhering to these steps, businesses can develop a clear view of their IT environment, which facilitates informed decision-making when selecting options that align with their strategic objectives.
When selecting IT solutions, healthcare organizations must adhere to that ensure effective outcomes.
By ensuring that selected IT approaches align closely with business objectives, medical institutions can cultivate a more integrated and effective operational environment, ultimately leading to improved patient care and institutional efficiency.
To ensure staff are well-prepared to utilize new IT solutions, healthcare organizations must implement effective strategies that resonate with their unique challenges.
By prioritizing comprehensive training and support, healthcare organizations can significantly enhance staff competency and confidence, which is crucial for businesses it. This leads to improved utilization of IT resources and ultimately better patient care.
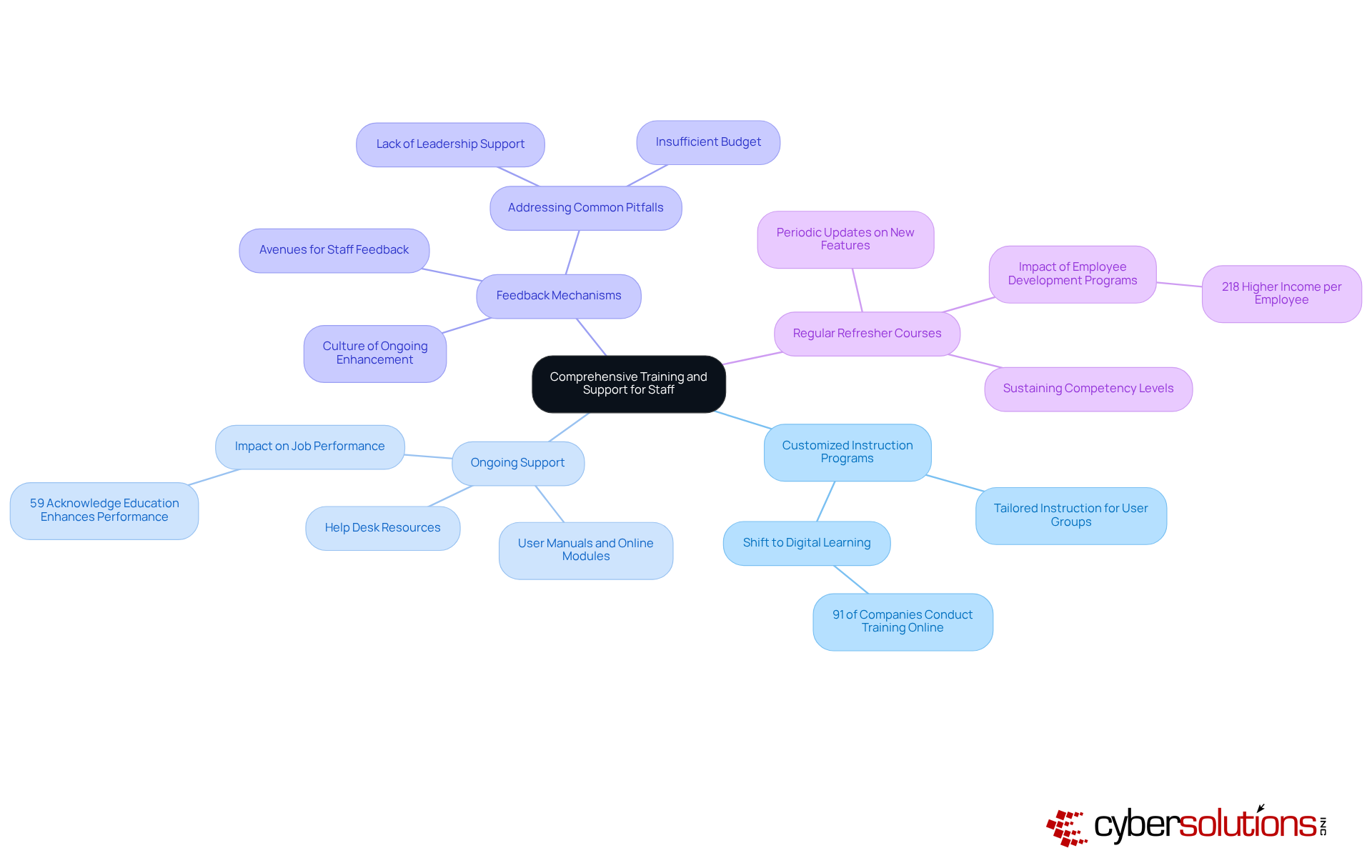
Healthcare organizations must adopt a proactive strategy for evaluating and optimizing their IT solutions, as businesses it focuses on key practices that drive effectiveness and adaptability.
Establishing Key Performance Indicators (KPIs): Defining specific metrics is essential to assess the effectiveness of IT approaches in meeting organizational objectives. For instance, tracking patient satisfaction scores and operational efficiency metrics can provide valuable insights into system performance and areas for improvement. According to Waleed A. Hassen, MD, MBA, "KPIs empower organizations to identify inefficiencies, implement evidence-based improvements, and demonstrate value to stakeholders."
Conducting Regular Audits: Implementing a schedule for periodic audits of IT systems is crucial for evaluating performance, security, and compliance with regulatory standards. Regular audits not only help identify vulnerabilities but also ensure that systems align with best practices and industry regulations. Partnering with experts in HIPAA compliance, such as Cyber Solutions, enhances this process by ensuring thorough documentation and proactive risk management, including detailed reporting and audit support.
Soliciting User Feedback: Actively gathering input from staff and stakeholders regarding the usability and effectiveness of IT systems is vital. This feedback informs future enhancements and ensures that systems meet user needs, ultimately leading to . A case study on "Technician Satisfaction" highlights how gathering user feedback can lead to a 20% increase in help desk efficiency.
Staying Informed on Industry Trends: Continuously monitoring emerging technologies and best practices in medical IT allows organizations to recognize opportunities for innovation and enhancement. By remaining informed, companies ensure their IT approaches stay pertinent and efficient in a swiftly changing environment. Additionally, understanding the role of cybersecurity in HIPAA compliance is essential, as it protects patient health information (PHI) from breaches and unauthorized access. Organizations should also consider the benefits of Compliance as a Service (CaaS), which provides ongoing support for audit preparation and continuous monitoring, helping to maintain compliance and security.
By committing to these practices, healthcare organizations can ensure their IT solutions are effective and adaptable to changing needs, thereby contributing to sustained operational success for businesses it supports.

Healthcare organizations encounter distinct challenges that necessitate customized IT solutions to boost operational efficiency and enhance patient care. This article delineates four best practices that can assist businesses in effectively evaluating their IT requirements and selecting suitable solutions. By engaging stakeholders, analyzing existing systems, ensuring regulatory compliance, and anticipating future needs, organizations can establish a robust framework for informed decision-making.
Moreover, aligning IT solutions with business objectives is crucial. By defining explicit goals, assessing vendor capabilities, ensuring scalability, and performing a comprehensive cost-benefit analysis, healthcare providers can choose technologies that not only tackle current challenges but also facilitate long-term growth. Furthermore, thorough training and ongoing support for staff are vital for maximizing the advantages of these IT investments, thereby nurturing a culture of continuous improvement.
In the swiftly evolving healthcare landscape, a commitment to regularly assess and optimize IT solutions is indispensable. By setting key performance indicators, conducting audits, seeking user feedback, and staying abreast of industry trends, organizations can ensure their IT systems remain effective and adaptable. Embracing these best practices not only enhances operational success but also ultimately leads to improved patient outcomes, reinforcing the critical role of strategic IT in the healthcare sector.
What is the first step in assessing organizational needs for IT solutions in healthcare?
The first step is stakeholder engagement, which involves involving key stakeholders from clinical, administrative, and IT departments to gather diverse perspectives on current challenges and desired outcomes.
Why is current system analysis important in the evaluation process?
Current system analysis is important because it involves a thorough review of existing IT infrastructure, software, and workflows to identify inefficiencies and areas for enhancement, helping organizations optimize their IT solutions.
What role does regulatory compliance play in assessing IT needs?
Regulatory compliance review is vital to ensure adherence to medical regulations such as HIPAA, which protects patient data and aligns with the scrutiny on medical data management.
How can organizations project their future IT needs?
Organizations can project future IT needs by anticipating technological requirements based on emerging trends in medical services, such as telemedicine and electronic health records (EHRs), to ensure their IT tools remain relevant and efficient.
What is the overall benefit of following these assessment steps?
By adhering to these steps, businesses can develop a clear view of their IT environment, facilitating informed decision-making when selecting options that align with their strategic objectives.