
Managed firewalls are indispensable for C-suite leaders, delivering enhanced security through continuous monitoring, scalability to accommodate business growth, and compliance support with regulatory requirements. In today's landscape of escalating cyber threats, organizations must prioritize these solutions to safeguard sensitive data and reduce operational costs. Furthermore, managed firewalls empower organizations to respond swiftly to cyber threats, fortifying their overall cybersecurity posture and ensuring business resilience. This strategic investment not only mitigates risks but also positions organizations to thrive in an increasingly complex regulatory environment.
In an era where cyber threats are more pronounced than ever, the necessity for robust security measures is paramount for organizations. Managed firewalls emerge as a critical solution, providing C-suite leaders with a comprehensive strategy to protect sensitive data while ensuring operational continuity. This article explores the ten key benefits of managed firewalls, illustrating how they not only strengthen defenses against emerging threats but also bolster business resilience and compliance.
As the cybersecurity landscape evolves, a pressing question arises: how can organizations effectively leverage these advanced solutions to navigate potential vulnerabilities and safeguard their assets?
Cyber Solutions Inc. offers a robust suite of managed firewalls that significantly enhance security for businesses across various sectors. These services are meticulously crafted to meet the unique needs of each industry, empowering organizations to protect sensitive data while maintaining operational efficiency. By leveraging the Zero Trust framework alongside advanced technologies, Cyber Solutions equips C-suite leaders with the insights necessary to make informed decisions regarding their cybersecurity investments. This proactive approach not only fortifies defenses against emerging threats but also bolsters overall business resilience.
With continuous of your network, Cyber Solutions identifies anomalies and potential vulnerabilities in real-time, enabling swift action to avert downtime or breaches. Immediate notifications and constant surveillance ensure that suspicious activities are detected and addressed before they escalate into significant threats. This is particularly vital for safeguarding businesses against ransomware, phishing, and other malware attacks, thereby maximizing ROI through customized IT and cybersecurity services. Furthermore, implementing access controls tailored to business requirements guarantees that only authorized users can access sensitive information.
As we approach 2025, the latest trends in managed security services spotlight the integration of artificial intelligence and machine learning, which enhance detection and response capabilities. These advancements empower organizations to stay ahead of potential cyber threats, minimizing risks and ensuring compliance with regulatory standards. The impact of managed firewalls on business safety is substantial, as they provide a critical layer of defense against data breaches and cyberattacks that can lead to significant financial losses and reputational damage.
Successful implementation of managed firewalls as part of security solutions has been demonstrated across various industries, including healthcare, finance, and manufacturing. For example, entities in the healthcare sector have utilized these services to comply with stringent regulations while safeguarding patient data. Similarly, financial organizations have adopted managed barriers to protect sensitive financial information, illustrating the adaptability and effectiveness of these solutions in enhancing protection frameworks. The recent merger between Clever Techs and Cyber Solutions further amplifies the capabilities offered, facilitating improved service delivery and operational capacity. By prioritizing controlled protection services, C-suite executives can ensure their organizations are well-equipped to navigate the complexities of modern cybersecurity challenges.
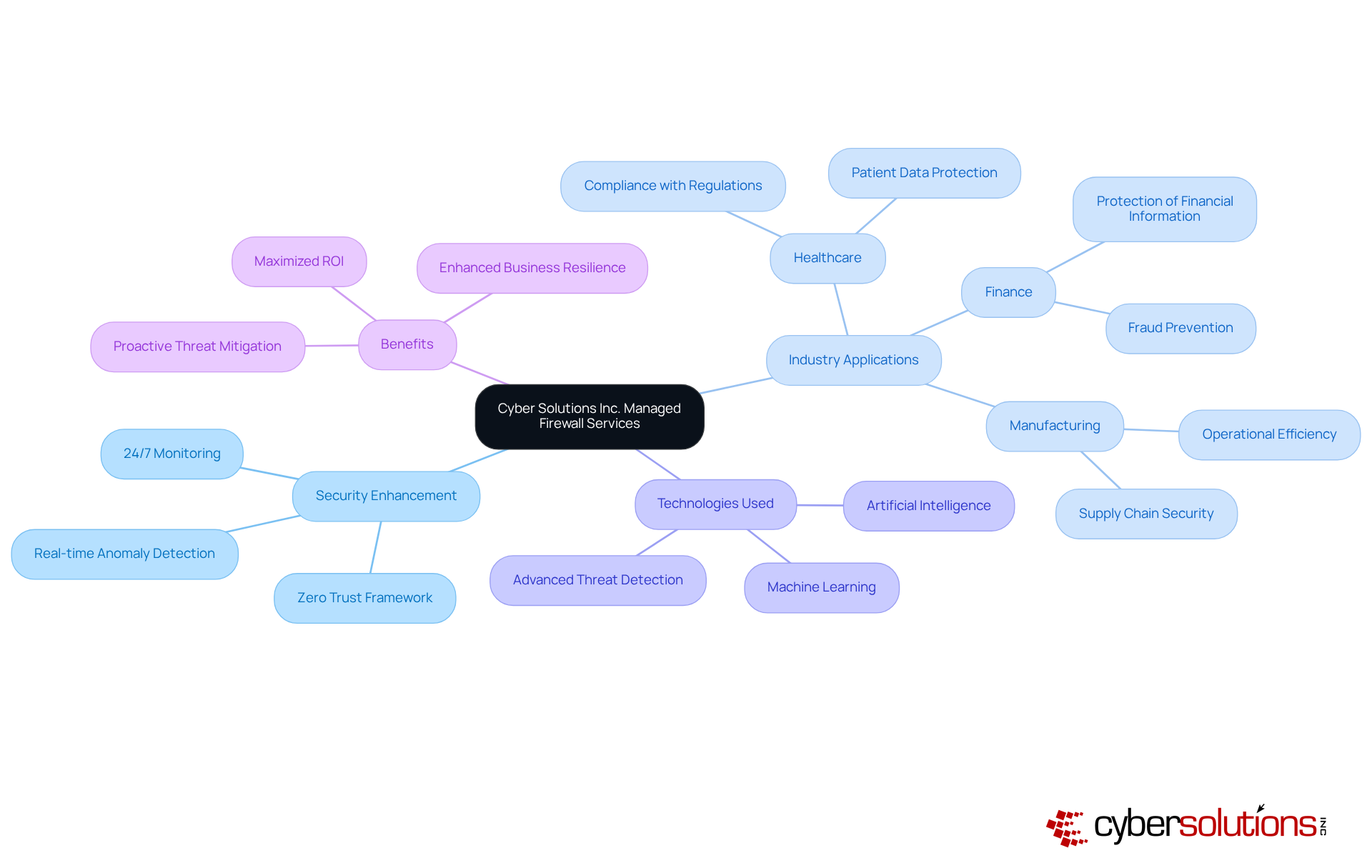
In an era where cybersecurity threats are increasingly sophisticated, it is a necessity to utilize managed firewalls from Cyber Solutions Inc. With , these services allow for proactive danger detection and swift responses to potential incidents. This continuous oversight is crucial, enabling organizations to identify and address suspicious activities before they escalate into significant breaches, thereby safeguarding both assets and reputation.
As we move into 2025, the emphasis on proactive danger detection becomes even more pronounced. Companies are increasingly recognizing that early identification of risks can drastically diminish the likelihood of incidents. For instance, organizations that implement comprehensive monitoring solutions report a notable decrease in breaches. Statistics reveal that timely detection can significantly reduce recovery costs, underscoring the value of these proactive measures.
Moreover, proactive risk identification not only enhances safety but also fosters customer confidence. Clients feel more secure knowing their sensitive information is consistently protected. By leveraging advanced technologies and expert oversight, Cyber Solutions empowers businesses to maintain operational continuity while effectively mitigating the risks associated with cyber threats. In this landscape, the question remains: Are you prepared to protect your organization from the ever-evolving cyber threats?
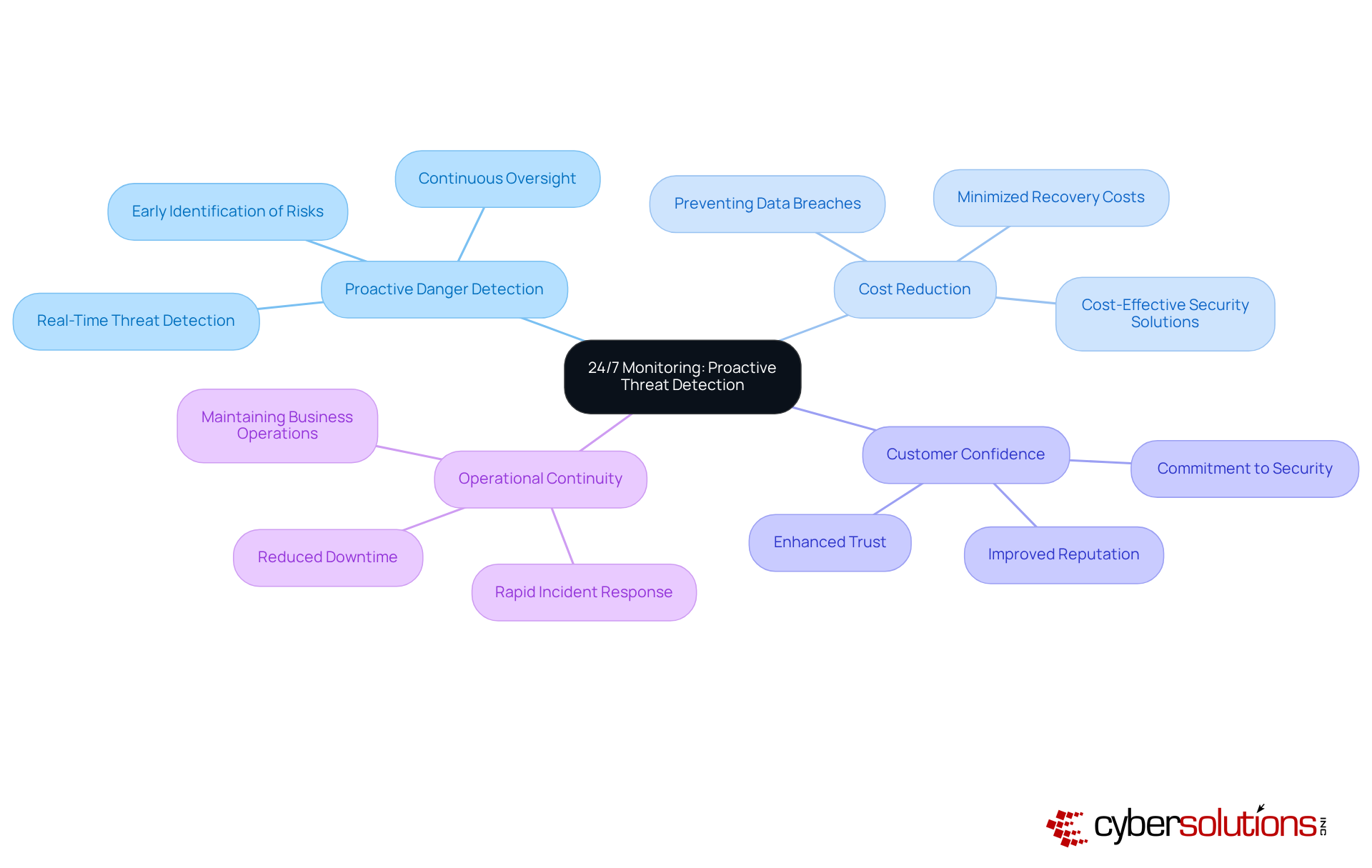
Managed networks are inherently scalable, enabling businesses to adjust their protective measures in tandem with growth. This adaptability is crucial as companies encounter new challenges and heightened demands, ensuring continuous protection without necessitating a complete overhaul of existing systems.
For instance, a logistics company that faced a close call with ransomware increased its cybersecurity spending by 15%, subsequently thwarting a similar attack the following year due to enhanced layered defenses. Furthermore, a manufacturing firm implemented a peer-led 'Security Champions' program, resulting in a 60% reduction in accidental data leaks within just six months.
These examples underscore the necessity for businesses to proactively adapt their cybersecurity measures as they expand, reinforcing that a is not merely a reactive measure but a foundational element of sustainable growth.
As entities evolve, the integration of managed firewalls enables effortless scalability, ensuring that protection protocols remain efficient and aligned with operational goals. Incorporating application allowlisting into your protection strategy further enhances this scalability by proactively preventing unauthorized software from executing. This includes features such as:
These features significantly reduce the attack surface and assist organizations in meeting stringent compliance requirements, such as HIPAA and GDPR. By restricting the applications that can operate, businesses can effectively safeguard against malware and ransomware, ensuring that their growth does not compromise safety.
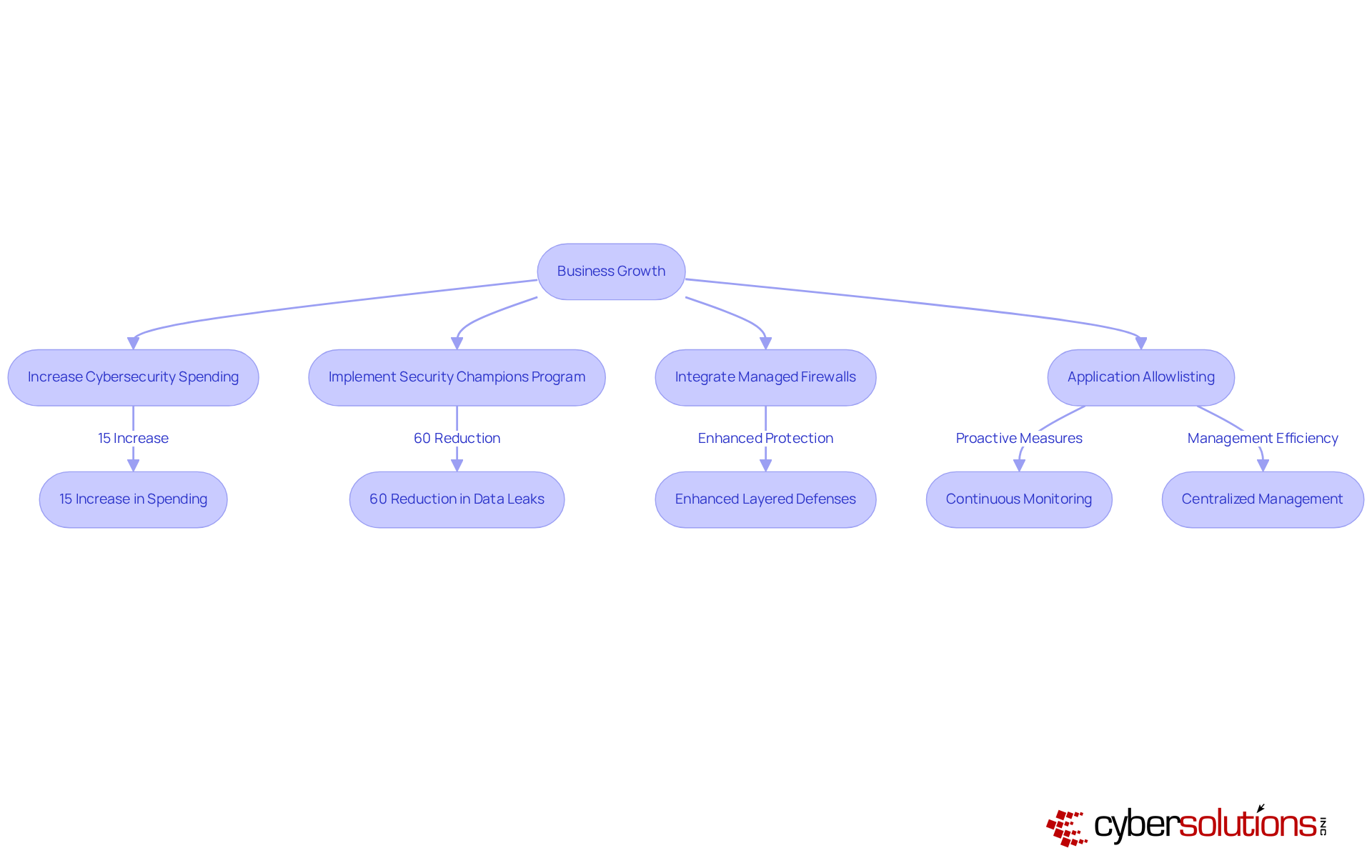
Investing in managed firewalls is crucial for organizations aiming to significantly lower operational costs while mitigating the risk of costly data breaches and downtime. By actively overseeing threats to safety, companies can avoid the financial repercussions associated with cyber incidents, making managed firewalls a cost-effective choice for securing business functions. Moreover, Cyber Solutions' flat-rate pricing model simplifies the budgeting process for businesses, eliminating unexpected IT expenses and ensuring predictable monthly costs.
This comprehensive approach not only enhances operational efficiency but also integrates , such as application allowlisting, which proactively prevents malware and unauthorized software from executing. By implementing these solutions, organizations can achieve robust protection while ensuring compliance with stringent regulations. In a landscape where cybersecurity threats are ever-evolving, the need for effective management and proactive measures has never been more critical.
In today's digital landscape, managed firewalls are crucial for organizations striving to comply with essential regulatory frameworks such as HIPAA, PCI-DSS, and GDPR. These frameworks impose significant obligations, and businesses that implement robust protective measures alongside tailored remediation strategies not only demonstrate compliance but also significantly mitigate the risk of incurring substantial penalties. For instance, non-compliance with GDPR can lead to fines of up to €20 million, while violations of PCI-DSS may result in monthly penalties ranging from $5,000 to $100,000.
Organizations leveraging managed security systems often report enhanced reputations among clients and stakeholders, showcasing their commitment to safeguarding sensitive data. A notable example is a healthcare provider that, after establishing managed barriers, achieved compliance and fortified its security posture, thereby reducing the likelihood of future breaches. As cybersecurity regulatory requirements evolve, it becomes imperative for organizations to maintain compliance through advanced protection solutions.
By employing managed firewalls as part of their security systems, companies can ensure they remain audit-ready and resilient against potential threats, ultimately fostering trust and confidence in their operations. This proactive approach not only but also positions organizations favorably in an increasingly scrutinized industry.

In today's rapidly evolving digital landscape, cybersecurity is paramount for organizations seeking to protect sensitive information and maintain operational integrity. Cyber Solutions Inc. emphasizes the seamless compatibility of its managed firewalls with existing IT systems, empowering companies to bolster their protective measures without necessitating extensive infrastructure modifications. This integration minimizes operational disruptions, enabling businesses to sustain efficiency while benefiting from .
For instance, organizations can implement next-generation firewalls (NGFWs) that function effortlessly alongside legacy systems, ensuring that critical processes remain uninterrupted. The advantages of such seamless compatibility are significant:
Notably, data indicates that major disturbances often accompany infrastructure renovations, with many organizations facing operational challenges that could lead to financial repercussions.
By prioritizing smooth integration, Cyber Solutions Inc. equips organizations to refine their cybersecurity strategies in 2025 and beyond, ensuring resilience against evolving threats while maintaining operational continuity. As the landscape of cybersecurity threats continues to shift, organizations must act decisively to safeguard their assets and ensure they are prepared for the challenges ahead.
In today's rapidly evolving cybersecurity landscape, organizations must prioritize their digital defenses. By choosing managed firewalls from Cyber Solutions Inc., businesses gain access to a team of skilled security professionals dedicated to safeguarding their assets. This expertise ensures that organizations are equipped with the most current knowledge and resources to confront emerging challenges, providing reassurance for C-suite leaders.
With of networks to detect anomalies and potential vulnerabilities, Cyber Solutions delivers instant alerts and real-time insights that facilitate swift action, preventing downtime or breaches. As cybersecurity risks continue to develop, the importance of adept management in addressing these challenges cannot be overstated.
Moreover, the layered approach to cybersecurity, which includes rapid incident response strategies as demonstrated in various case studies, underscores the effectiveness of having a dedicated incident response team. This team is always ready to act, ensuring that threats are contained and recovery is swift. In a world where the stakes are high, investing in managed firewalls is not just a choice; it is a necessity for resilient operations.
In today's rapidly evolving digital landscape, the importance of cybersecurity cannot be overstated. Managed firewalls play a pivotal role in streamlining regular updates and maintenance activities, ensuring that protective measures remain current without necessitating ongoing manual involvement. This automation not only enhances security but also frees up internal resources, allowing teams to focus on strategic initiatives rather than day-to-day maintenance. Given that ransomware incidents affect 72.7% of organizations annually, the urgency of adopting automated updates becomes starkly clear. Furthermore, misconfiguration problems contribute to as much as 99% of security breaches, as highlighted by Gartner analysts, underscoring how automation can significantly mitigate such risks.
Ongoing oversight of your network is essential; it guarantees that suspicious actions are identified and halted before they escalate into serious threats, delivering immediate notifications and real-time information for prompt response. Continuous monitoring of security measures is crucial, as it ensures that protective strategies adapt to evolving dangers. Moreover, organizations that leverage automated security systems can reap substantial financial benefits, including minimized downtime and enhanced staff productivity. Ultimately, this not only but also boosts operational efficiency.
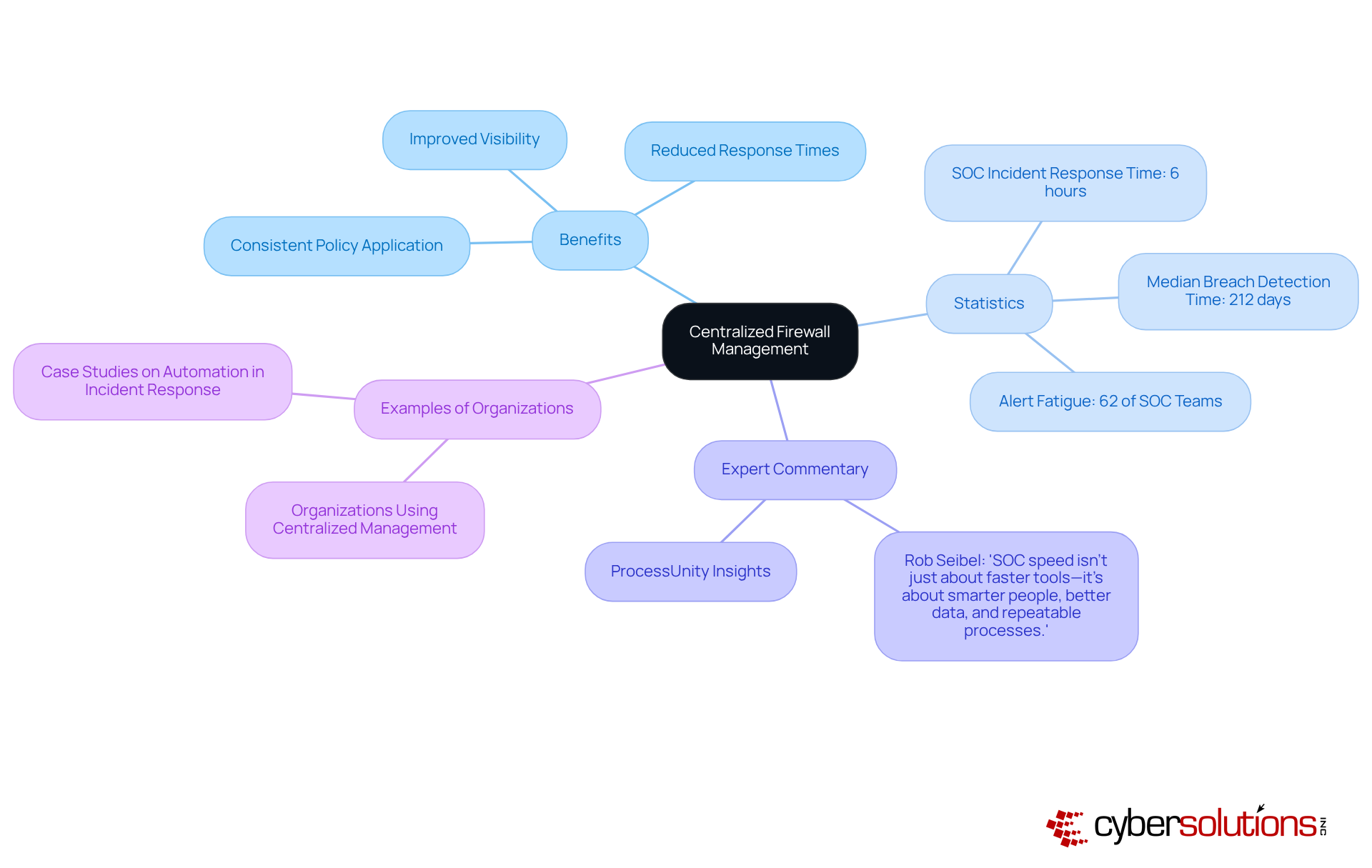
In today's rapidly evolving cybersecurity landscape, entities can benefit from managed firewalls that offer essential centralized management functionalities, allowing them to oversee protective measures from a unified platform. This approach significantly enhances visibility and control, allowing for quicker reactions to potential risks. Indeed, organizations that implement centralized management for security typically experience a reduction in response times, with the average Operations Center (SOC) addressing incidents in roughly six hours. However, the median time to detect a breach can extend to 212 days, highlighting the urgent need for improved efficiency in threat detection and response.
Centralized administration ensures that protective policies are consistently applied across the organization, thereby minimizing the risk of misconfigurations that could lead to vulnerabilities. As cybersecurity expert Rob Seibel aptly states, "SOC speed isn’t just about faster tools—it’s about smarter people, better data, and repeatable processes." This comprehensive strategy not only simplifies operations but also strengthens the overall security posture of the organization.
Organizations that streamline their management of firewalls through centralized oversight include those that have adopted integrated protective systems, which consolidate managed firewalls, access controls, and monitoring tools into a single interface. This integration not only enhances administrative efficiency but also improves the effectiveness of protective measures, allowing teams to focus on high-priority threats while alleviating the burden of , a challenge faced by 62% of SOC teams. By leveraging centralized oversight, entities can fortify their cybersecurity frameworks and respond more adeptly to the dynamic threat landscape.
In the ever-evolving landscape of healthcare, managed firewalls are not just beneficial—they are essential. They provide swift incident response capabilities that significantly mitigate the damage during a breach. Cyber Solutions Inc. equips organizations with the necessary tools and strategies to act decisively, thereby minimizing the impact of incidents and safeguarding valuable assets from further harm.
As we move into 2025, the average reaction time to breaches has emerged as a crucial metric. Organizations that employ managed firewalls report response times that are 30% faster than those lacking such measures. This rapid response not only facilitates the restoration of normal operations but also plays a pivotal role in and ensuring compliance with regulatory standards like HIPAA, PCI-DSS, and GDPR.
Consider a recent incident where a client utilizing Cyber Solutions' managed security services successfully isolated a threat within minutes. This decisive action drastically reduced potential damage and downtime, underscoring the necessity of investing in robust firewall solutions to enhance overall security posture and ensure business continuity.
Moreover, with continuous monitoring for threats, businesses can identify and respond to suspicious activities before they escalate into significant risks. This proactive approach is vital in safeguarding against ransomware, phishing, and other malware attacks. Organizations must also prioritize compliance documentation and staff training to effectively combat evolving threats and achieve and maintain HIPAA compliance.
In conclusion, the imperative for healthcare organizations is clear: investing in managed firewalls not only fortifies security but also ensures resilience in the face of increasing cyber threats. The time to act is now.
Investing in managed firewalls is not just a choice; it is a strategic imperative for C-suite leaders dedicated to fortifying their organization's cybersecurity posture. These solutions deliver robust protection against a multitude of cyber threats, empowering executives to make informed decisions regarding their cybersecurity investments. By integrating managed firewalls, businesses can establish a proactive defense strategy that aligns seamlessly with their operational goals and growth trajectories.
The article underscores several pivotal benefits of managed firewalls:
Furthermore, the incorporation of advanced technologies like AI and machine learning allows organizations to stay ahead of potential threats, while centralized management streamlines oversight and enhances response times to incidents.
The significance of managed firewalls is paramount. As cyber threats evolve, organizations must prioritize their digital defenses to protect sensitive information and uphold operational integrity. By leveraging managed firewall services, businesses not only safeguard their assets but also cultivate trust and confidence among clients and stakeholders. The call to action is unequivocal: now is the moment for executives to invest in comprehensive cybersecurity solutions that guarantee resilience and security in an increasingly complex digital landscape.
What services does Cyber Solutions Inc. offer?
Cyber Solutions Inc. offers a comprehensive suite of managed firewall services designed to enhance security for businesses across various sectors, focusing on protecting sensitive data while maintaining operational efficiency.
How does Cyber Solutions Inc. ensure security for businesses?
The company utilizes the Zero Trust framework and advanced technologies, providing continuous 24/7 monitoring to identify anomalies and vulnerabilities in real-time, enabling swift responses to potential threats.
What are the benefits of 24/7 monitoring?
24/7 monitoring allows for proactive threat detection and swift responses to suspicious activities, helping to prevent significant breaches and safeguarding both assets and reputation.
How do managed firewalls help in compliance with regulations?
Managed firewalls assist businesses, particularly in sectors like healthcare and finance, in complying with stringent regulations while protecting sensitive information, thereby enhancing their overall security frameworks.
What is the significance of scalability in managed firewalls?
Scalability in managed firewalls allows businesses to adjust their protective measures as they grow, ensuring continuous protection without needing complete system overhauls.
Can you provide examples of how businesses have benefited from managed firewalls?
A logistics company increased its cybersecurity spending after a ransomware scare and successfully thwarted a similar attack the following year. A manufacturing firm implemented a 'Security Champions' program, resulting in a 60% reduction in accidental data leaks within six months.
What technologies are being integrated into managed security services?
The latest trends emphasize the integration of artificial intelligence and machine learning to enhance detection and response capabilities, helping organizations stay ahead of potential cyber threats.
How do managed firewalls reduce the attack surface?
Features like application allowlisting prevent unauthorized software from executing, which helps in reducing the attack surface and meeting compliance requirements such as HIPAA and GDPR.
What impact do managed firewalls have on business resilience?
Managed firewalls provide a critical layer of defense against cyberattacks, significantly reducing the risk of data breaches and financial losses, thus bolstering overall business resilience.
How does Cyber Solutions Inc. support C-suite leaders in decision-making?
By providing insights through their managed firewall services, Cyber Solutions Inc. empowers C-suite leaders to make informed decisions regarding their cybersecurity investments, enhancing their strategic planning.