
In 2025, the landscape of cybersecurity is more critical than ever, particularly for C-suite leaders who must navigate the complexities of protecting their organizations. The article identifies the top managed firewall solutions, underscoring their essential role in enhancing cybersecurity measures. Leading providers such as:
are highlighted for their advanced features and compliance capabilities. These robust managed firewall services not only mitigate cyber threats effectively but also offer significant financial benefits, making them a strategic investment for organizations aiming to bolster their cybersecurity posture. By understanding the unique challenges faced by healthcare organizations, C-suite leaders can make informed decisions that prioritize security and compliance while driving operational efficiency.
In an era where cyber threats are increasingly sophisticated and pervasive, the necessity for robust cybersecurity measures has never been more critical for organizations across all sectors. This article explores the top managed firewall solutions tailored for C-suite leaders in 2025, emphasizing how these services not only protect digital assets but also enhance operational efficiency and compliance. As businesses confront escalating risks, the pressing challenge remains: how can leaders effectively navigate the complex cybersecurity landscape to safeguard their organizations while maximizing ROI?
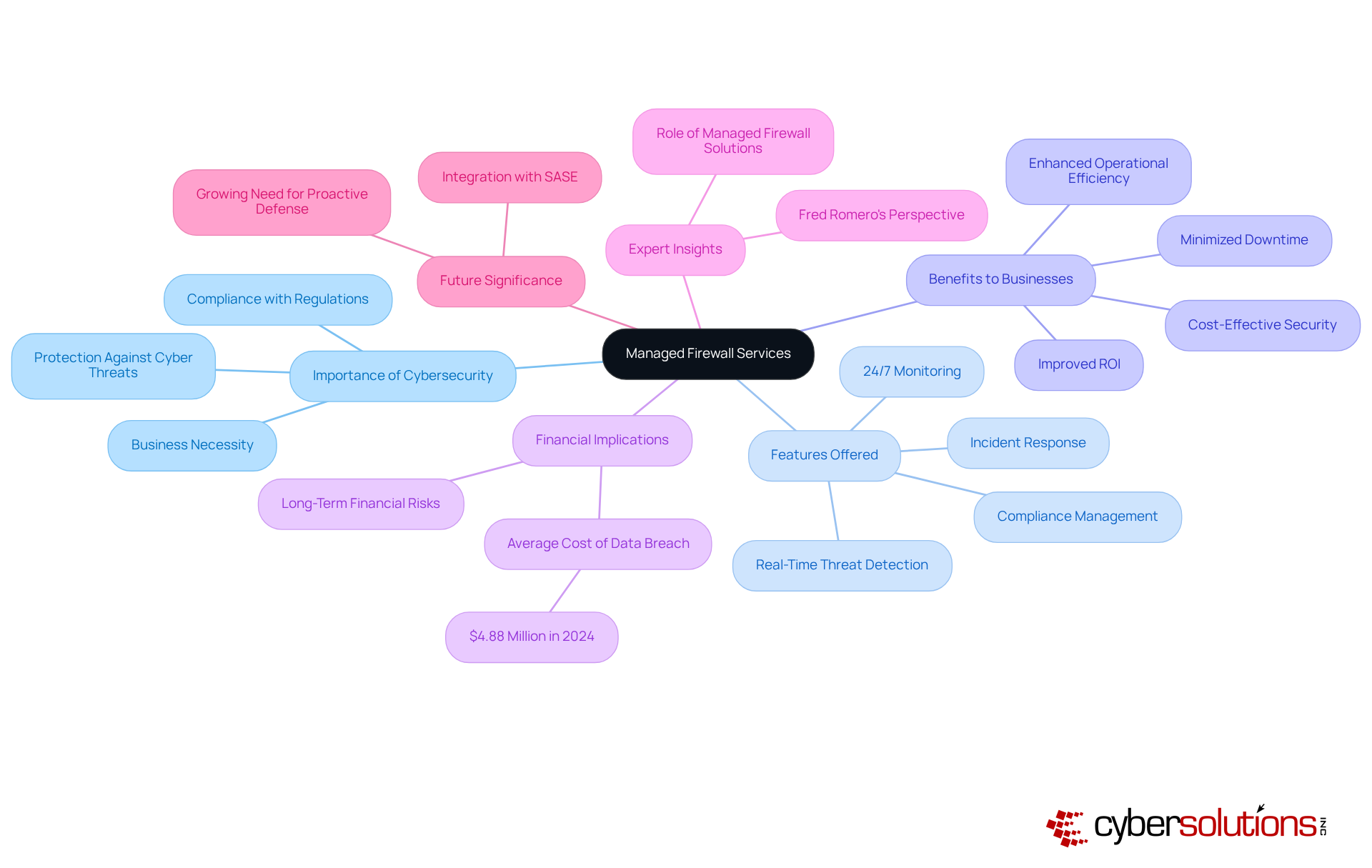
In today's rapidly evolving digital landscape, the importance of cybersecurity cannot be overstated—especially for businesses operating in sensitive sectors like healthcare. Cyber Solutions offers a comprehensive suite of managed security services designed to protect organizations from the ever-changing threats posed by cybercriminals. With robust features such as , incident response, and compliance management, businesses can concentrate on their core operations without the burden of IT protection weighing them down. The financial implications are significant; in 2024, the average cost of a data breach reached $4.88 million, underscoring the necessity for strong security measures to mitigate financial risks.
The benefits of Cyber Solutions' managed security services extend far beyond mere protection. These services enhance operational efficiency and ensure compliance with regulatory standards, ultimately improving ROI by minimizing both downtime and associated costs. For instance, organizations in the finance and healthcare sectors, which are particularly susceptible to cyberattacks, can leverage these services to adhere to stringent data protection regulations. A stark reminder of the vulnerabilities faced by organizations lacking adequate cybersecurity measures is the cyberattack on the London nursery chain Kido.
Cybersecurity experts emphasize the critical role of managed firewall solutions in today's digital environment. As Fred Romero, a recognized authority in enterprise IT infrastructure, states, "Cybersecurity is no longer an option—it's a business necessity in the modern digital landscape." This perspective resonates across various industries, reinforcing the essential nature of managed firewall solutions in protecting against unauthorized access, malware, and other malicious threats. Insights from additional cybersecurity professionals further highlight the imperative of these solutions for protecting digital assets.
Looking ahead to 2025, the significance of managed firewall solutions will only continue to grow as organizations increasingly recognize the need for proactive defense strategies. By partnering with Cyber Solutions, businesses can ensure they are equipped with cutting-edge technologies and expert knowledge, enhancing their defensive posture and effectively safeguarding their digital assets.
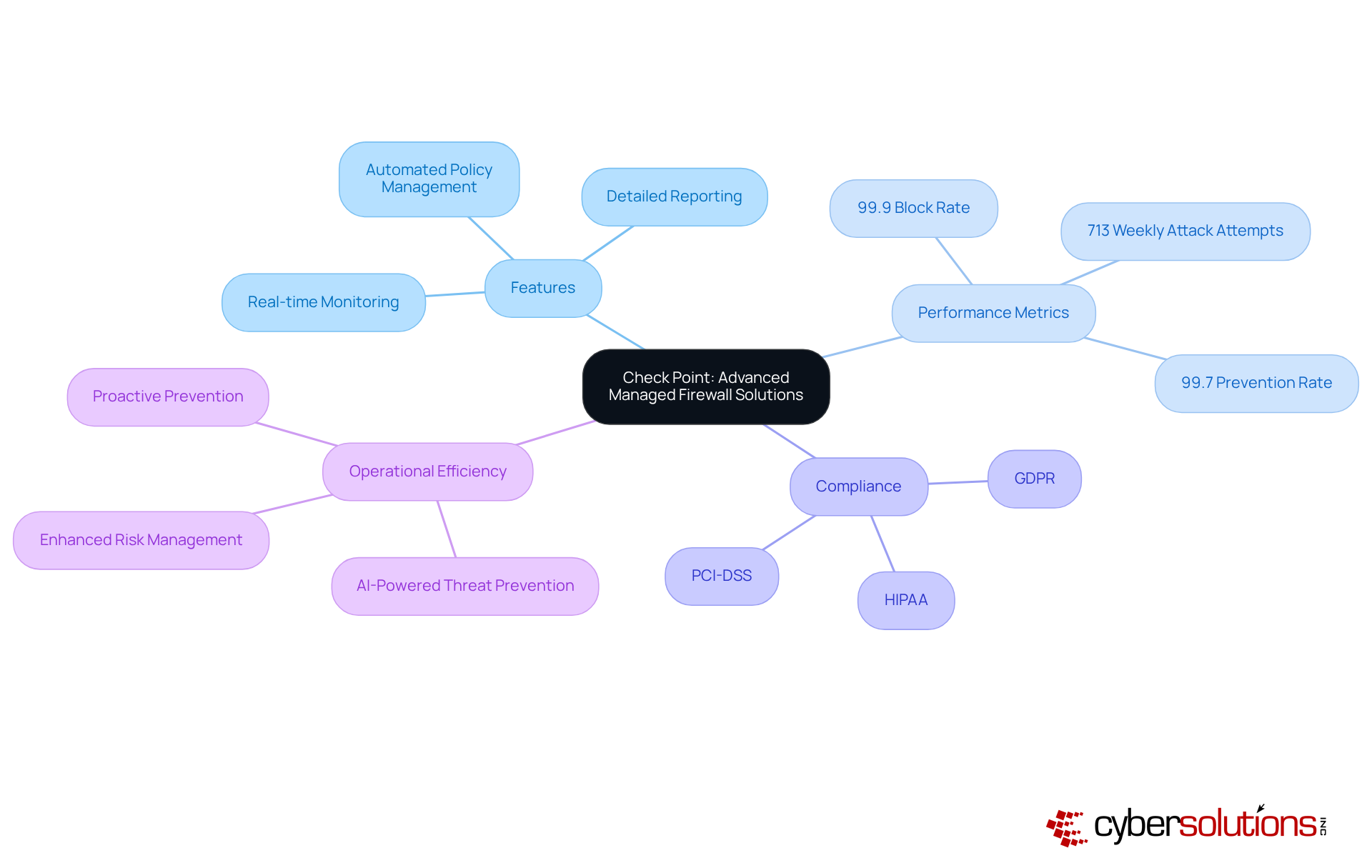
In today's digital landscape, the importance of cybersecurity cannot be overstated, particularly in sectors like healthcare where sensitive data is at stake. Check Point provides advanced managed firewall solutions that utilize state-of-the-art threat prevention technologies, ensuring strong protection against a wide range of cyber threats. Their solutions encompass:
All meticulously designed to enhance network security and facilitate compliance with industry regulations. Notably, the Check Point Infinity Platform has achieved an impressive 99.9% block rate against Zero+1 day malware and a 99.7% prevention rate for phishing, underscoring its effectiveness in safeguarding organizations.
Moreover, the integration of application allowlisting into managed firewall solutions by Check Point significantly enhances their effectiveness. This proactive approach prevents unauthorized or malicious applications from executing, thereby reducing the attack surface and minimizing vulnerabilities. By ensuring that only pre-approved software can operate, companies can effectively block malware, ransomware, and zero-day attacks before they can inflict damage. This capability is essential for meeting stringent compliance requirements such as HIPAA, PCI-DSS, and GDPR, which are crucial for organizations aiming to secure federal contracts.
Industry specialists recognize Check Point's innovations as pivotal in addressing contemporary safety challenges. For instance, the introduction of AI-powered Quantum Force Branch Office Security Gateways has markedly improved threat prevention performance, offering up to a fourfold increase compared to previous models. This advancement is critical, especially as branch offices encounter an average of 713 weekly attack attempts, reflecting a 36% increase from the previous year.
For C-suite leaders, this signifies that investing in Check Point's solutions not only mitigates risks but also enhances operational efficiency by reducing the likelihood of costly incidents. The incorporation of Check Point's solutions into existing IT infrastructures empowers organizations to transition from reactive remediation to proactive prevention, thus improving their overall defense posture. With a steadfast commitment to continuous improvement, Check Point's technologies not only but also enable businesses to navigate the complexities of today's digital landscape with confidence.
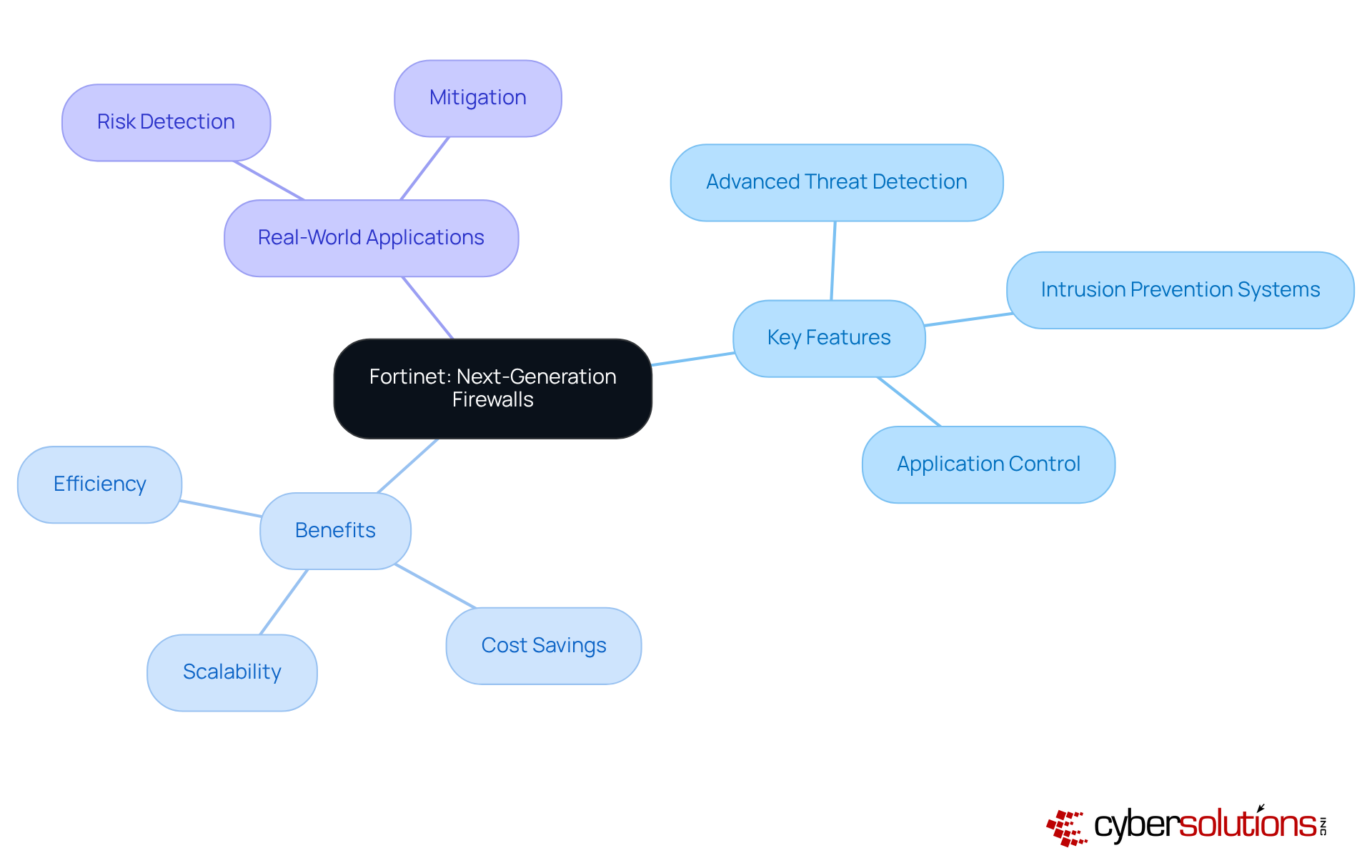
Fortinet's next-generation systems redefine protection, emphasizing the critical importance of cybersecurity in today's landscape. These managed firewall solutions provide a comprehensive range of features that extend well beyond conventional network defenses, incorporating advanced threat detection, intrusion prevention systems, and application control. Each element is meticulously designed to counter sophisticated cyber threats, ensuring organizations are well-equipped to face the evolving risks.
With at their core, Fortinet's managed firewall solutions can be customized to meet the distinct needs of various entities. This adaptability makes them an ideal choice for companies seeking to enhance their security posture while efficiently utilizing managed firewall solutions and managing expenses. Notably, organizations utilizing Fortinet firewalls have reported significant cost savings, with some achieving up to 62% lower power consumption per Gbps of IPsec VPN throughput compared to industry standards. Such efficiency not only boosts operational performance but also contributes to a more sustainable IT infrastructure.
Real-world applications further demonstrate the effectiveness of Fortinet's advanced risk detection capabilities, which have proven essential in identifying and mitigating potential breaches before they escalate. As cybersecurity risks continue to evolve, Fortinet remains at the forefront of innovation, consistently updating its features to ensure robust protection for its clients in 2025 and beyond. This commitment to excellence positions Fortinet as a trusted partner in navigating the complexities of cybersecurity.
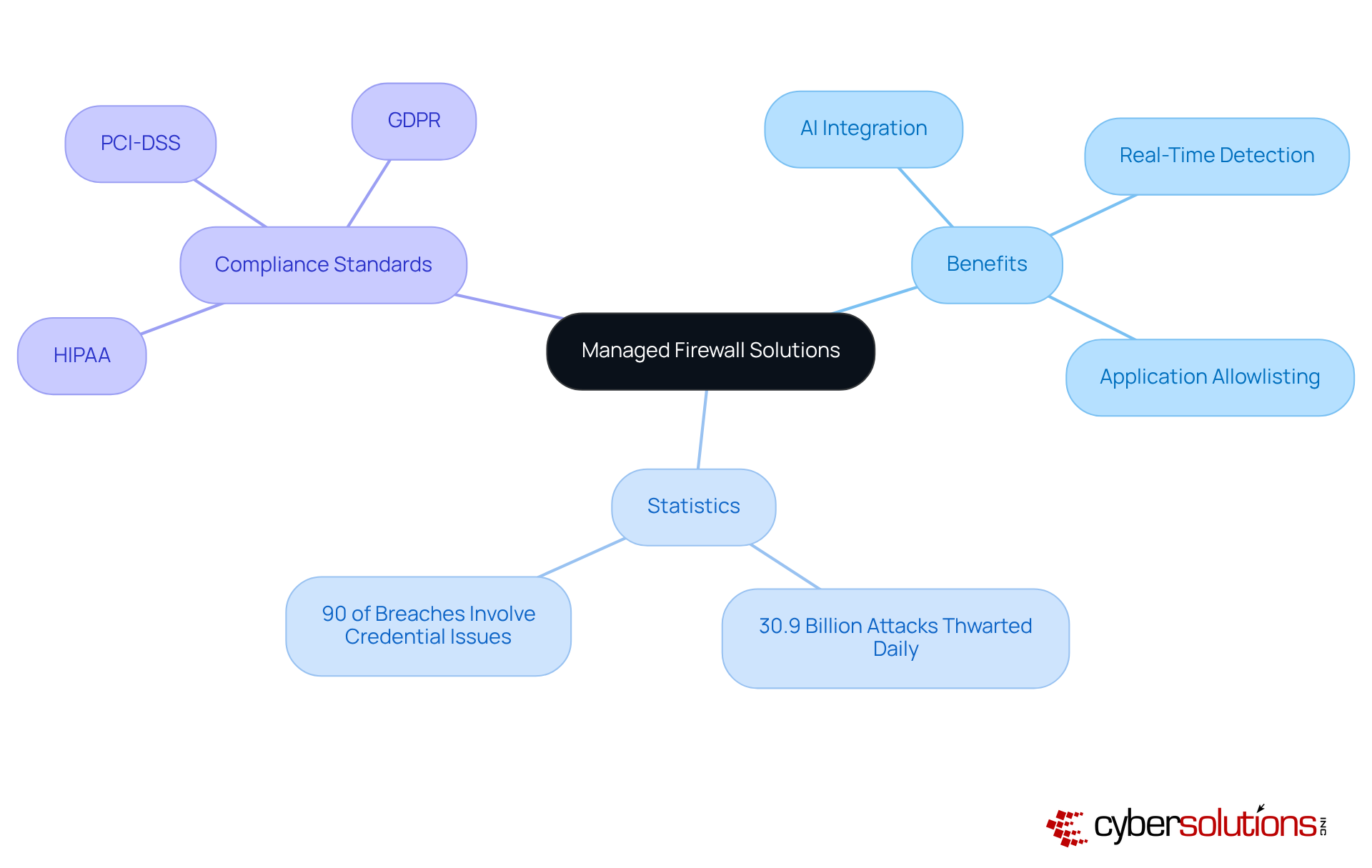
In today's digital landscape, the significance of robust cybersecurity measures cannot be overstated, particularly in the healthcare sector. Cyber Solutions provides innovative managed firewall solutions that harness the power of artificial intelligence and machine learning, greatly enhancing detection and response capabilities. These advanced managed firewall solutions provide comprehensive visibility into network traffic, enabling organizations to swiftly identify and neutralize threats in real-time. Coupled with application allowlisting, which proactively prevents malware and unauthorized software from executing, our solutions effectively reduce the attack surface and minimize vulnerabilities.
With over 30.9 billion inline attacks thwarted each day and the alarming fact that over 90% of breaches involve stolen or poorly managed credentials, the need for is critical. By focusing on automation and seamless integration, Cyber Solutions' offerings not only streamline operational processes but also ensure compliance with industry standards such as:
Furthermore, the launch of the Quantum Readiness Dashboard exemplifies our proactive strategy to safeguard investments against emerging challenges.
As CEO Nikesh Arora aptly stated, 'As more and more critical applications and data reside within the browser, it naturally becomes a target for cyberattacks.' This underscores the necessity of integrating advanced security measures, including application allowlisting, in today's digital environment. With a commitment to continuous improvement, Cyber Solutions stands at the forefront of cybersecurity innovation, empowering organizations to navigate the complexities of modern threats effectively.
In today's rapidly evolving landscape, cybersecurity has emerged as a paramount concern for organizations, particularly in highly regulated sectors. Cyber Solutions excels in providing managed firewall solutions that not only emphasize compliance with industry regulations but also ensure that entities can maintain a secure environment. Their offerings encompass:
As we approach 2025, the focus on compliance becomes critical; indeed, 68% of business leaders acknowledge increasing cybersecurity risks, prompting further investments in risk management. As noted by Consilien IT Company, "A solid IT partner will help you avoid those costs while keeping your systems secure and compliant." By prioritizing compliance, Cyber Solutions effectively mitigates risks related to data breaches and cyber challenges, establishing itself as a trusted partner for organizations operating in highly regulated sectors.
Their solutions simplify navigating regulatory requirements. These services provide:
Real-world instances of their vulnerability evaluations illustrate a proactive method for recognizing and tackling potential risks, reinforcing the effectiveness of their cybersecurity strategies. Furthermore, their incident response services significantly reduce the impact of cyberattacks by quickly identifying, containing, and alleviating risks, thereby ensuring business continuity.
As compliance continues to shape the landscape of cybersecurity, Cyber Solutions' tailored solutions—including incident response capabilities and compliance support—position businesses to navigate these challenges successfully. Organizations seeking to enhance their cybersecurity posture must consider the critical role of compliance in their overall strategy.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, particularly within the healthcare sector. Cyber Solutions excels in delivering customized managed firewall solutions that enhance network control and security for diverse businesses, including those in healthcare, finance, manufacturing, and government. Their solutions are meticulously designed to meet the distinct needs of each entity, featuring capabilities such as:
For instance, in a recent case, Cyber Solutions' incident response team effectively contained a significant risk within hours, showcasing their prowess in real-world scenarios.
As we look to 2025, industry data highlights a crucial trend: over 70% of entities prioritize customized protective measures to effectively tackle evolving cyber threats. Cyber Solutions' flexible strategy enables organizations to establish protective measures that seamlessly integrate with their operational structures, ensuring comprehensive defense against a wide array of cyber threats. Industry experts advocate for managed firewall solutions, noting that they not only enhance security but also improve operational efficiency. This allows businesses to concentrate on their core activities while maintaining robust defenses.
Moreover, Cyber Solutions' guaranteed four-hour service level agreement (SLA) underscores their commitment to client support, ensuring prompt assistance that minimizes potential downtime. This dedication to dependability and rapid response solidifies Cyber Solutions as a favored choice for entities seeking . In a world where cyber threats are ever-evolving, the need for tailored cybersecurity measures has never been more critical.
In today's rapidly evolving digital landscape, cybersecurity is not just an option; it is a necessity. CyberMaxx provides its NexGen Firewall as a Service, delivering organizations managed firewall solutions that adapt to the shifting risk landscape. This service includes continuous monitoring, threat intelligence, and , ensuring comprehensive protection against emerging cyber threats.
Statistics from 2025 indicate that organizations employing proactive incident response strategies can reduce breach expenses by an impressive average of $1.49 million. This underscores the financial benefits of such measures. Moreover, companies that conduct incident response drills at least quarterly respond to incidents 35% faster, emphasizing the critical role of preparedness in effective cybersecurity management.
By leveraging advanced technology and managed firewall solutions, CyberMaxx empowers organizations to enhance their protection stance while improving operational efficiency. This positions CyberMaxx as an indispensable ally in navigating the complexities of modern cybersecurity challenges.

In today's digital landscape, the importance of cybersecurity cannot be overstated. Cyber Solutions offers robust managed firewall solutions designed to protect organizations from a wide array of cyber risks. Their comprehensive solutions include:
These features empower businesses to respond swiftly to potential safety incidents. With and alerts, Cyber Solutions enables organizations to sustain a secure environment, significantly reducing the risk of data breaches.
Their advanced cybersecurity offerings encompass:
All tailored to safeguard sensitive data against emerging threats. Given that nearly 80% of businesses are either highly or moderately concerned about the likelihood of a cyberattack in the coming year, the establishment of effective managed firewall solutions is crucial. C-suite executives must critically evaluate their current security measures and consider the integration of managed firewall solutions to enhance their cybersecurity posture and maximize ROI.
By addressing these pressing challenges, Cyber Solutions positions itself as a vital partner in the fight against cyber threats, ensuring that organizations can thrive in an increasingly perilous digital environment.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, particularly for organizations reliant on technology. Synergy IT Solutions offers round-the-clock managed firewall solutions, complete with advanced reporting features that provide essential insights into network protection. These managed firewall solutions are meticulously designed to , enabling companies to swiftly identify and address potential threats. Continuous monitoring and detailed reporting are at the core of Synergy's strategy, ensuring that businesses not only maintain a secure environment but also adhere to stringent industry regulations.
As we look ahead to 2025, entities leveraging extensive reporting capabilities can expect a significant reduction in response times to incidents. Currently, the average duration to recognize and manage breaches stands at an alarming 277 days. Cybersecurity specialists emphasize that efficient reporting functionalities are vital for companies to keep pace with emerging threats and bolster their overall defense posture. By choosing Synergy IT Solutions, organizations can take proactive steps toward safeguarding their operations and enhancing their cybersecurity resilience.
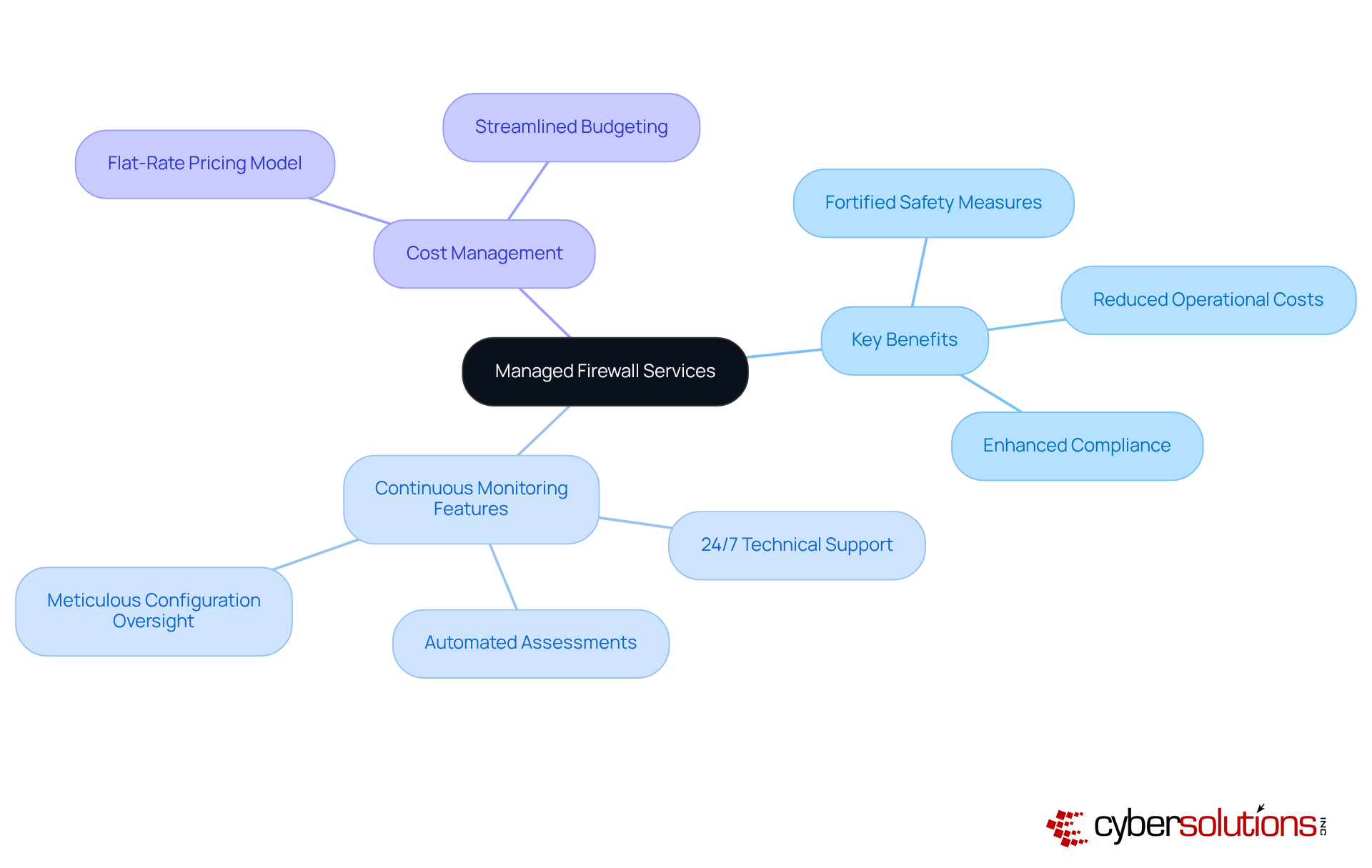
In today's digital landscape, the significance of robust cybersecurity cannot be overstated. Cyber Solutions underscores the primary advantages of managed protective services, which include:
By entrusting network security management to specialists, organizations benefit from continuous monitoring, featuring:
This proactive approach significantly mitigates the risk of data breaches.
Our comprehensive managed IT and cybersecurity solutions empower businesses with the adaptability to scale their security measures according to evolving needs, ensuring formidable protection amidst an ever-changing threat environment. Moreover, our flat-rate pricing model streamlines budgeting by removing unexpected IT expenses, enabling companies to allocate resources more effectively.
Furthermore, organizations that have embraced managed firewall solutions from Cyber Solutions report considerable decreases in operational costs. This emphasizes that managed firewall solutions are an essential element of , reinforcing the need for organizations to prioritize their cybersecurity frameworks.
In a world where cybersecurity is paramount, C-suite leaders must prioritize managed firewall solutions to protect their organizations from an increasingly sophisticated array of cyber threats. This article highlights the significance of these solutions, illustrating how they not only safeguard sensitive data but also enhance operational efficiency and compliance across various industries. As businesses gear up for 2025, investing in robust managed firewall services is essential for maintaining a secure digital environment.
Key arguments presented throughout the article emphasize the diverse offerings from leading providers such as:
Each solution is tailored to meet the unique needs of organizations, providing features like:
The financial implications of neglecting cybersecurity are clear, with potential data breaches costing millions. Thus, the integration of these services is not just a protective measure but a strategic business decision.
As organizations navigate the complexities of modern cybersecurity challenges, the call to action is clear: prioritize the adoption of managed firewall solutions to fortify defenses and ensure compliance with industry standards. By doing so, businesses position themselves to thrive in a digital landscape fraught with risks, ultimately safeguarding their assets and promoting long-term success.
What are managed firewall services and why are they important for businesses?
Managed firewall services are cybersecurity solutions that protect organizations from cyber threats through features like 24/7 monitoring, incident response, and compliance management. They are essential for businesses, especially in sensitive sectors like healthcare, to mitigate risks and ensure the security of their digital assets.
What financial impact do data breaches have on businesses?
In 2024, the average cost of a data breach reached $4.88 million, highlighting the financial risks that businesses face without strong cybersecurity measures in place.
How do Cyber Solutions' managed security services benefit organizations?
Cyber Solutions' services enhance operational efficiency, ensure compliance with regulatory standards, and improve ROI by minimizing downtime and associated costs, particularly for sectors like finance and healthcare that are vulnerable to cyberattacks.
What features do Check Point's managed firewall solutions offer?
Check Point's managed firewall solutions include real-time monitoring, automated policy management, and detailed reporting features, all designed to enhance network security and facilitate compliance with industry regulations.
How effective is the Check Point Infinity Platform against cyber threats?
The Check Point Infinity Platform boasts a 99.9% block rate against Zero+1 day malware and a 99.7% prevention rate for phishing, demonstrating its effectiveness in safeguarding organizations from cyber threats.
What role does application allowlisting play in Check Point's firewall solutions?
Application allowlisting prevents unauthorized or malicious applications from executing, thereby reducing vulnerabilities and minimizing the attack surface. This capability is crucial for meeting compliance requirements such as HIPAA, PCI-DSS, and GDPR.
What advancements has Check Point made in threat prevention technologies?
Check Point has introduced AI-powered Quantum Force Branch Office Security Gateways, which significantly improve threat prevention performance, offering up to a fourfold increase compared to previous models.
How do Fortinet's next-generation firewalls enhance security?
Fortinet's next-generation firewalls incorporate advanced threat detection, intrusion prevention systems, and application control, providing comprehensive protection against sophisticated cyber threats.
What cost benefits do organizations experience with Fortinet's managed firewall solutions?
Organizations using Fortinet firewalls have reported significant cost savings, with some achieving up to 62% lower power consumption per Gbps of IPsec VPN throughput compared to industry standards.
How does Fortinet stay ahead in cybersecurity innovation?
Fortinet continuously updates its features to address evolving cybersecurity risks, ensuring robust protection for its clients and positioning itself as a trusted partner in navigating cybersecurity complexities.