
In today's rapidly evolving digital landscape, the integration of Endpoint Detection and Response (EDR) into cybersecurity strategies is not just beneficial; it is essential. As cyber threats become increasingly sophisticated, organizations must adopt robust defenses to safeguard their sensitive information.
EDR tools offer:
These features collectively reduce the risk of data breaches and significantly enhance organizational resilience. By leveraging EDR, businesses can proactively address emerging threats, ensuring they remain one step ahead in the cybersecurity battle.
In an age where cyber threats are becoming increasingly sophisticated, organizations face the daunting task of safeguarding their digital assets against relentless attacks. Endpoint Detection and Response (EDR) has emerged as a pivotal solution, offering real-time monitoring and rapid response capabilities that are essential for maintaining robust cybersecurity.
As businesses strive to enhance their security posture, the pressing question arises: how can they effectively integrate EDR into their existing frameworks to maximize its benefits and minimize vulnerabilities?
This article delves into the critical components of EDR, its operational mechanisms, and best practices for implementation, providing a roadmap for organizations determined to fortify their defenses in an evolving threat landscape.
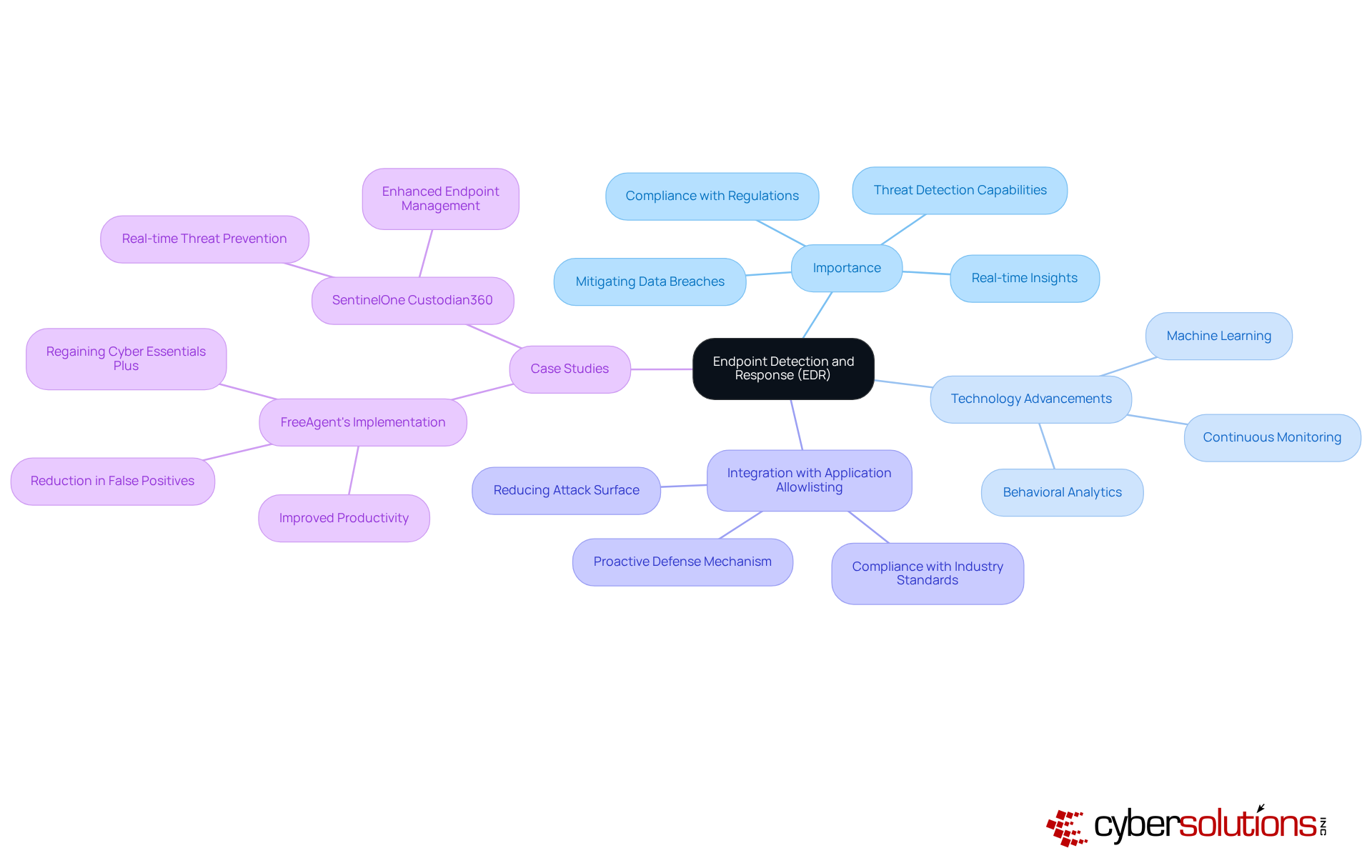
EDR cyber represents a critical suite of cybersecurity tools and processes designed to monitor, detect, and respond to threats targeting endpoint devices, including computers, mobile devices, and servers. EDR solutions furnish real-time insights into endpoint activities, empowering organizations to swiftly identify and address suspicious behaviors. The significance of EDR cyber is underscored by its sophisticated threat detection capabilities, which are essential for bolstering a company’s security posture, mitigating the risk of data breaches, and ensuring compliance with industry regulations.
As we look ahead to 2025, advancements in EDR cyber technology have firmly established its position as a fundamental component of cybersecurity strategies. These methodologies leverage machine learning and behavioral analytics to uncover threats that traditional antivirus software may overlook, providing organizations with a proactive defense mechanism against increasingly sophisticated cyber threats. Experts assert that EDR cyber is not merely an enhancement; it is a necessity for organizations committed to protecting sensitive data and maintaining operational integrity.
In conjunction with EDR, application allowlisting is regarded as the gold standard in cybersecurity. This strategy proactively prevents unauthorized or malicious applications from executing, significantly and minimizing vulnerabilities. Application allowlisting permits only approved applications to run while continuously monitoring all application activity to identify any attempts to launch unauthorized software. This method not only aids in blocking malware, ransomware, and zero-day attacks but also ensures compliance with stringent regulations such as HIPAA, PCI-DSS, and GDPR. The integration of application allowlisting with EDR cyber solutions enhances the overall security framework, providing robust protection against cyber threats.
Case studies illustrate the transformative impact of EDR on organizational safety. For example, FreeAgent's adoption of the SentinelOne Custodian360 solution resulted in a notable reduction in false positives, enabling employees to operate more efficiently and regain Cyber Essentials Plus accreditation. This not only boosted productivity but also reinforced the company’s commitment to data protection within a highly regulated environment. Conor MacHugh, Systems and Security Engineer, remarked, "Working with CWSI has resulted in FreeAgent having practically zero productivity issues, which is a welcomed change from our previous experience."
Furthermore, statistics indicate that organizations using EDR cyber solutions experience a significant decrease in data breaches. Continuous monitoring and rapid response capabilities enable teams to act promptly, often reducing the average time between a breach and detection, which can exceed 200 days without such measures. By integrating EDR cyber and application allowlisting into their cybersecurity frameworks, businesses can proactively defend against attacks, minimize potential damage, and enhance their overall security posture.
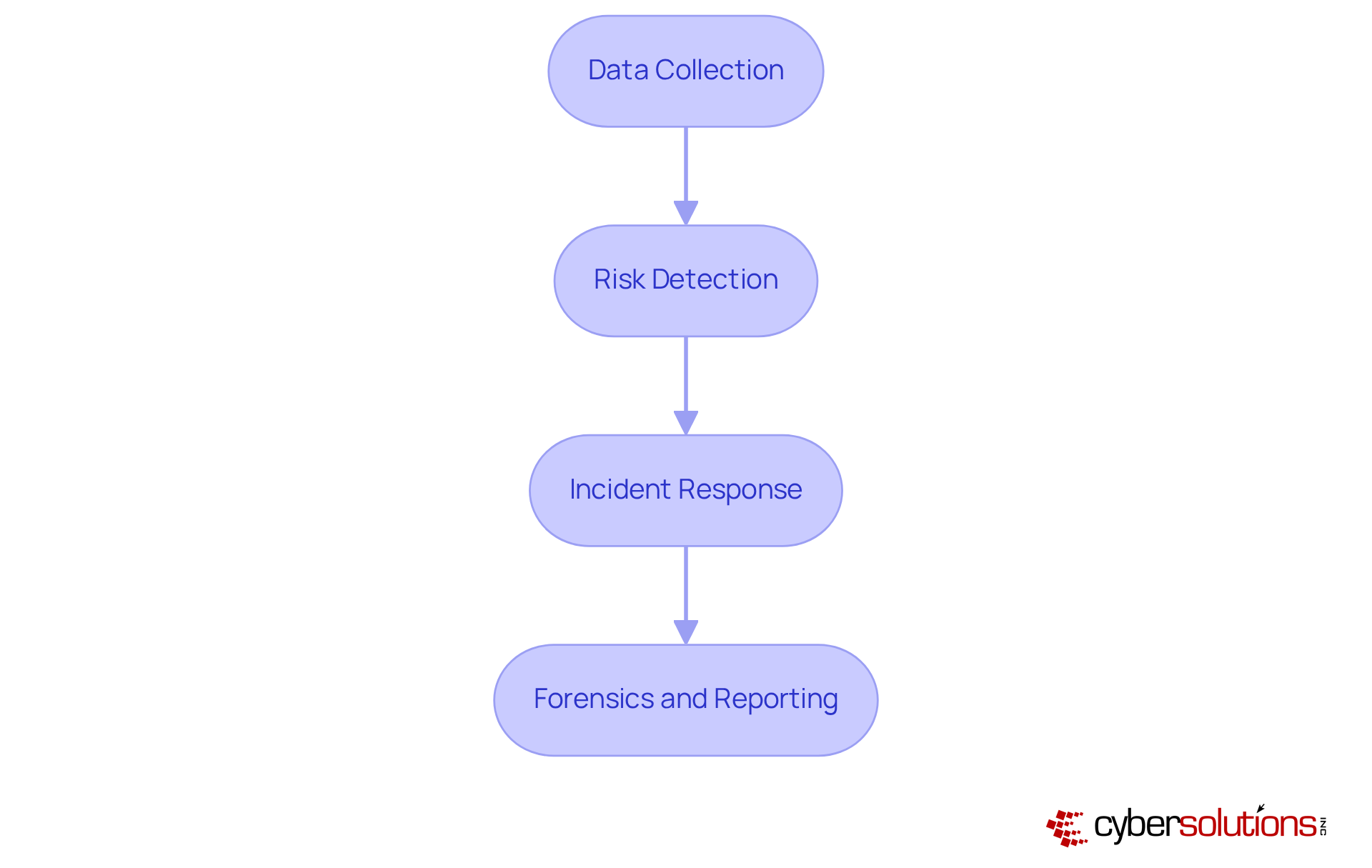
In the ever-evolving landscape of cybersecurity, understanding the mechanisms behind EDR solutions is crucial for organizations aiming to safeguard their digital assets. EDR solutions operate through a sophisticated interplay of data collection, analysis, and response mechanisms. They continuously monitor endpoint activities and network connections, gathering telemetry data on processes and files. This data is analyzed using advanced algorithms and machine learning methods, enabling the identification of anomalies that may indicate potential risks. Ongoing observation ensures that dubious actions are detected and mitigated before they escalate into significant threats, thus protecting your organization from ransomware, phishing, and other malware attacks through advanced threat intelligence.
Upon detecting a potential threat, EDR systems can by isolating the affected endpoint, blocking harmful processes, or alerting security teams for further investigation. The key processes involved in EDR include:
By comprehending these mechanisms, organizations can appreciate the essential role EDR plays in fortifying their cybersecurity strategies, particularly as the threat landscape continues to evolve.
When implementing EDR cyber solutions, organizations must prioritize several key features and best practices to enhance their cybersecurity posture.
Regular updates and threat intelligence are crucial for the EDR cyber solution to stay updated with the latest information and maintain an advantage against emerging threats and vulnerabilities. Organizations must prioritize this to maintain a proactive security stance.
Best practices for EDR cyber implementation involve conducting a thorough assessment of your organization's specific needs before selecting an EDR solution to ensure alignment with security objectives. Training your security team on the functionalities of the EDR tool is essential to maximize its effectiveness and ensure proper utilization. Additionally, regularly reviewing and updating incident response plans based on insights gained from EDR data is vital for maintaining agility in response strategies. Engaging in continuous monitoring and improvement of EDR processes allows organizations to adapt to evolving threats, leveraging data analytics for informed decision-making.
Case studies illustrate the effectiveness of these practices. For instance, FreeAgent's application of the SentinelOne Custodian360 solution resulted in a notable decrease in false positives, thereby improving productivity and defensive stance. This deployment not only regained their Cyber Essentials Plus accreditation but also underscored the importance of integrating EDR with existing security measures for comprehensive protection. As entities encounter progressively advanced cyber threats, embracing these best practices for EDR cyber implementation is crucial for enhancing overall cybersecurity strategies.

To effectively integrate Endpoint Detection and Response (EDR) into your cybersecurity strategy, organizations must recognize the critical importance of robust defenses in today's digital landscape. With 31% of entities reporting , the urgency for strong protective frameworks has never been clearer.
By implementing these essential steps, organizations can successfully integrate EDR into their cybersecurity strategies, significantly bolstering their defenses against cyber threats and ensuring a proactive stance in an increasingly complex digital landscape.

EDR cyber has become a critical component in today’s cybersecurity landscape, equipping organizations with essential tools to detect, respond to, and mitigate threats aimed at endpoint devices. As cyber threats evolve in sophistication, integrating Endpoint Detection and Response into cybersecurity strategies is not merely optional; it is a vital necessity for protecting sensitive data and ensuring operational integrity.
This article has underscored the significance of EDR through its advanced threat detection capabilities, real-time monitoring, and automated response mechanisms. The collaboration between EDR and application allowlisting further strengthens the security framework, significantly decreasing the attack surface and enhancing compliance with regulatory standards. Case studies, such as that of FreeAgent, illustrate the tangible benefits of implementing EDR solutions, showcasing reduced false positives and improved productivity. Furthermore, statistics indicate a notable decline in data breaches among organizations employing these technologies.
In conclusion, the urgency for robust cybersecurity measures cannot be overstated. Organizations must assess their current security posture, define clear objectives for EDR implementation, and promote collaboration across teams to bolster the effectiveness of their cybersecurity strategies. By adopting EDR cyber solutions and adhering to best practices, businesses can not only defend against existing threats but also prepare to adapt to the ever-evolving landscape of cyber risks. Taking proactive measures today will ensure a more secure tomorrow.
What is Endpoint Detection and Response (EDR)?
EDR is a suite of cybersecurity tools and processes designed to monitor, detect, and respond to threats targeting endpoint devices like computers, mobile devices, and servers.
Why is EDR important for organizations?
EDR is important because it provides real-time insights into endpoint activities, allowing organizations to swiftly identify and address suspicious behaviors, thereby bolstering their security posture and mitigating the risk of data breaches.
How does EDR improve threat detection?
EDR improves threat detection by leveraging machine learning and behavioral analytics to uncover threats that traditional antivirus software may overlook, offering a proactive defense against sophisticated cyber threats.
What is application allowlisting and how does it relate to EDR?
Application allowlisting is a cybersecurity strategy that prevents unauthorized or malicious applications from executing by allowing only approved applications to run. When integrated with EDR, it enhances overall security by reducing the attack surface and minimizing vulnerabilities.
What are the benefits of using application allowlisting?
The benefits of application allowlisting include blocking malware, ransomware, and zero-day attacks, as well as ensuring compliance with regulations like HIPAA, PCI-DSS, and GDPR.
Can you provide an example of EDR's impact on an organization?
An example is FreeAgent's adoption of the SentinelOne Custodian360 solution, which led to a reduction in false positives, improved employee efficiency, and the regaining of Cyber Essentials Plus accreditation.
What statistics support the effectiveness of EDR solutions?
Statistics indicate that organizations using EDR experience a significant decrease in data breaches, with continuous monitoring and rapid response capabilities reducing the average time between a breach and detection, which can exceed 200 days without EDR measures.
How do EDR and application allowlisting work together?
EDR and application allowlisting work together to provide a comprehensive cybersecurity framework that proactively defends against attacks, minimizes potential damage, and enhances the overall security posture of businesses.